Basic Authentication is now the past in Exchange Online
Table of Contents
Basic authentication(Basic Auth) is a living legend that will soon become only a legend. Basic Auth has been an insecure authentication method for any service or application for a long time.
The combination of a username (now our email address) and a password is not a secure authentication method for regular day-to-day use in any context.
Microsoft's removal of Basic Auth from Exchange Online (EXO) is only the beginning. However, it would be best if you did not wait for vendors to disable it on your behalf.
Deprecation of Basic authentication in Exchange Online will be October 1, 2022
Cybersecurity frameworks and authentication
If you haven't noticed, I frequently refer to cybersecurity frameworks. I can recommend reading my post "What is a Cybersecurity framework" if you need a refresh.

Let's have a look at what each Security framework has to say about authentication.
NIST
IA-2 IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS)
- (1) Implement multi-factor authentication for access to non-privileged accounts. Discussion: Multi-factor authentication requires the use of two or more different factors to achieve authentication. The authentication factors are defined as follows: something you know (e.g., a personal identification number [PIN]), something you have (e.g., a physical authenticator such as a cryptographic private key), or something you are (e.g., a biometric).
CIS
CIS Control 6 - Access Control Management
- Require all externally-exposed enterprise or third-party applications to enforce MFA, where supported. Enforcing MFA through a directory service or SSO provider is a satisfactory implementation of this Safeguard.
Zero-trust by Microsoft (recommended to follow)
Authentication using strong authentication such as MFA
Advanced
- The majority of applications use cloud identity for authentication, authorization, provisioning, and deprovisioning.
- Transparency regarding identity and session risk.
Optimal (recommended)
- Authentication using methods that are passwordless and resistant to phishing.
- All apps should support modern or federated with cloud identity for authentication, authorization, provisioning, and deprovisioning.
- Automated access reviews ensure proper management of group memberships, access to apps, and role assignments
Basic Authentication in EXO?
I won't go into more detail about Basic Auth. It's just a username and password, and you should block it. But first, you need to know if your environment or users are actively using Basic Auth.
Basic Auth Messaging protocols.
- Authenticated SMTP - Used to send authenticated email messages.
- Autodiscover - Used by Outlook and EAS clients to find and connect to mailboxes in Exchange Online.
- Exchange ActiveSync (EAS) - Used to connect to mailboxes in Exchange Online.
- Exchange Online PowerShell - Used to connect to Exchange Online with remote PowerShell. If you block Basic authentication for Exchange Online PowerShell, you need to use the Exchange Online PowerShell Module to connect. For instructions, see Connect to Exchange Online PowerShell using multifactor authentication.
- Exchange Web Services (EWS) - A programming interface that's used by Outlook, Outlook for Mac, and third-party apps.
- IMAP4 - Used by IMAP email clients.
- MAPI over HTTP (MAPI/HTTP) - Primary mailbox access protocol used by Outlook 2010 SP2 and later.
- Offline Address Book (OAB) - A copy of address list collections that are downloaded and used by Outlook.
- Outlook Anywhere (RPC over HTTP) - Legacy mailbox access protocol supported by all current Outlook versions.
- POP3 - Used by POP email clients.
- Reporting Web Services - Used to retrieve report data in Exchange Online.
- Universal Outlook - Used by the Mail and Calendar app for Windows 10.
- Other clients - Other protocols identified as utilizing legacy authentication.
To keep things simple, I've created a two-step plan that will give you the information you need to disable Basic Auth.
- Understand the impact of blocking Basic Auth
- How to block Basic Auth for Exchange Online
Understand the impact of blocking Basic Auth
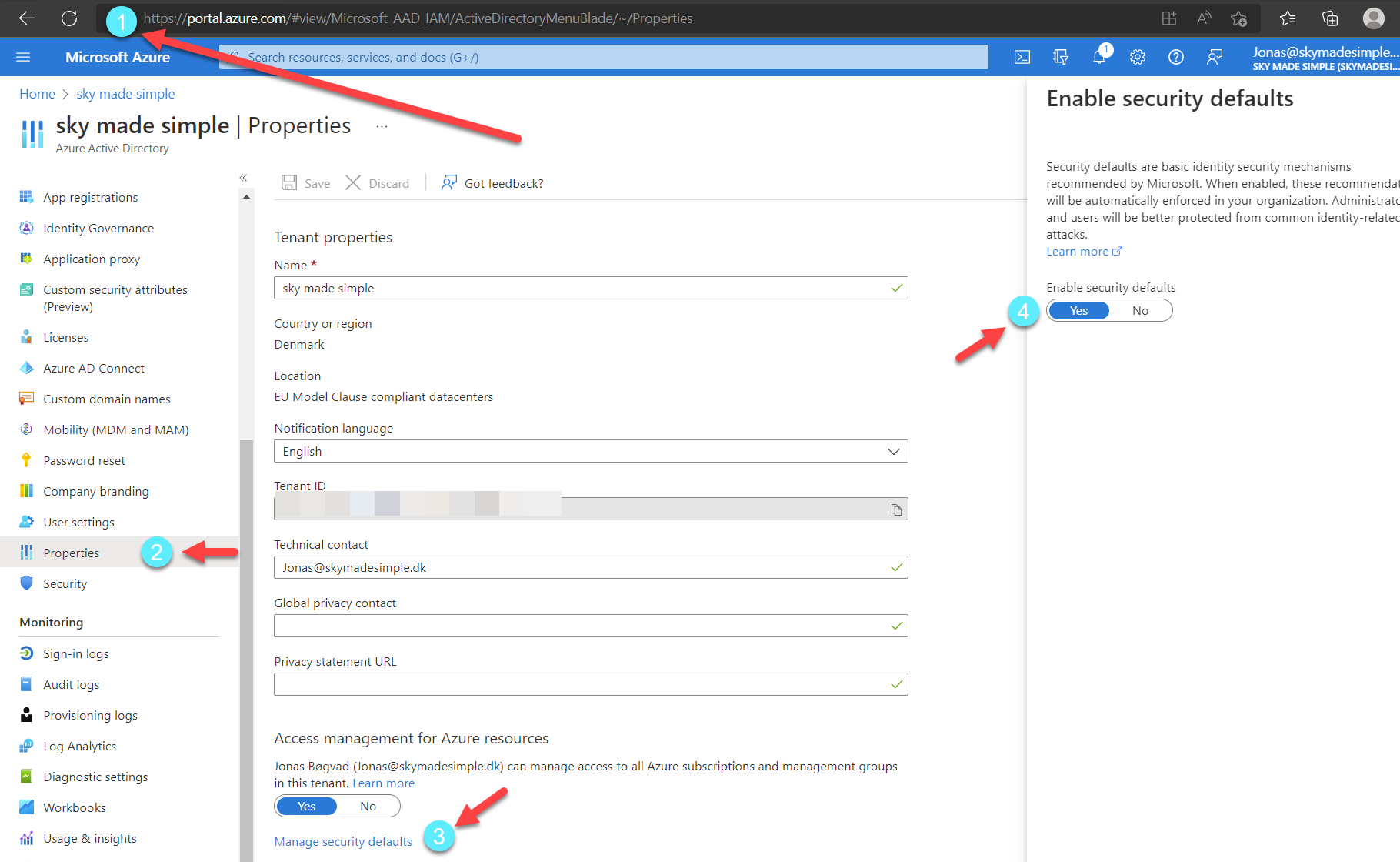
If you are using security defaults, basic auth is blocked for all services. See screenshot below to validate if you do use Security defaults.
- Go to portal.azure.com
- Go to properties
- Click on security defaults
- If yes, then its enabled. If no, then its disabled.
Service accounts
Consider service accounts that use Basic Authentication to send email. You can also review your script and search for the following when authentication occurs, which will also appear as Single-factor or Multi-factor auth in the sign-in logs.
- Get-Credential = Basic Auth = Single-factor auth
- Connect-ExchangeOnline = Modern Auth = Multi-factor auth
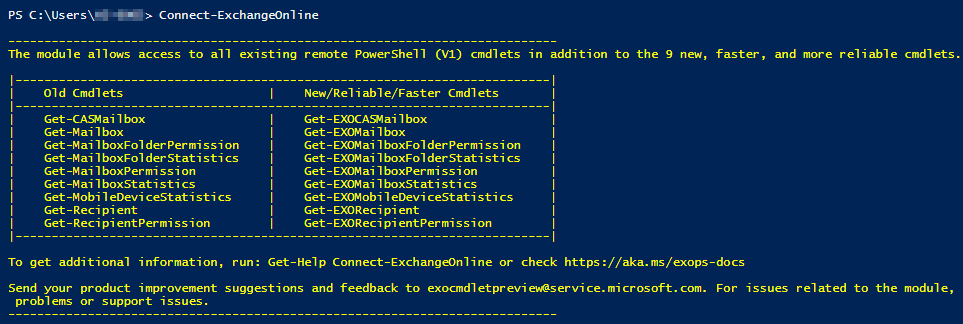
Microsoft released in 2021 a new EXO module that can run unattended and utilized Modern Auth called Exchange Online PowerShell V2 Module.
Managed identities
Unfortunately, the EXO PowerShell module V2 is not supported with managed identities yet.
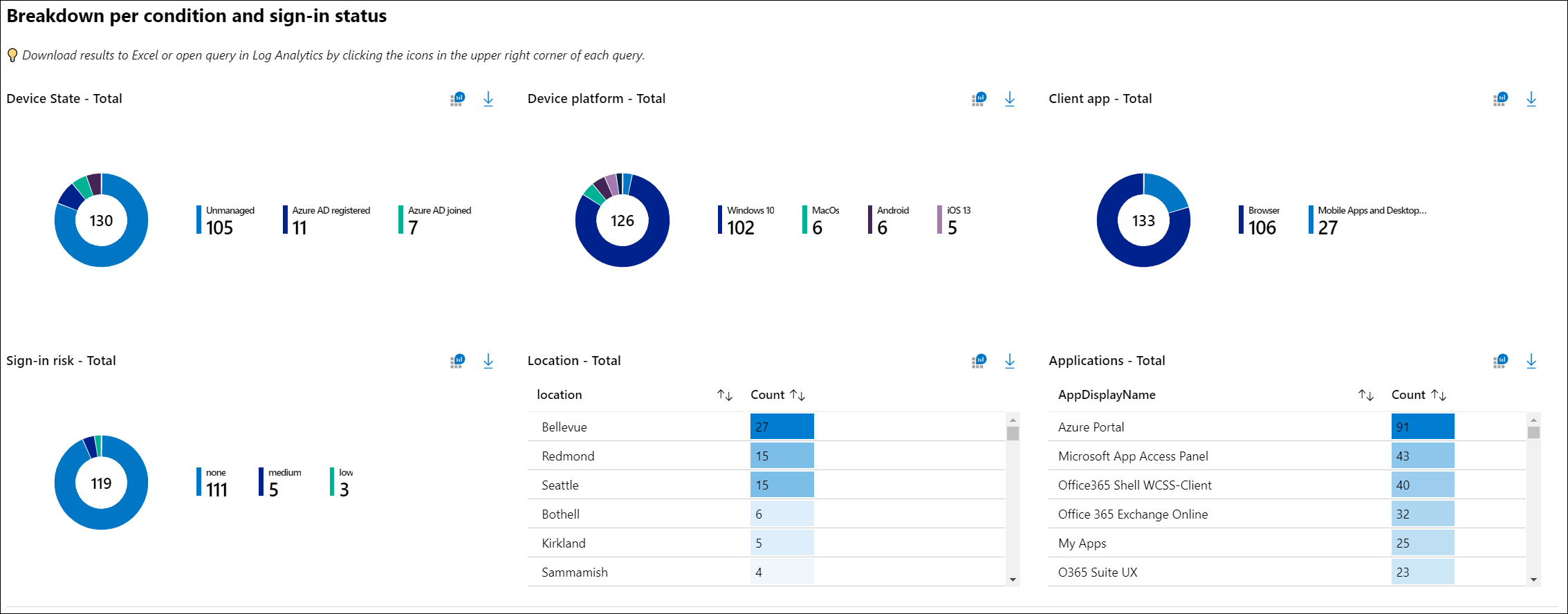
Sign-in logs
The easiest way to check if you are using Basic Auth in your environment is that you take a quick look at your Azure AD sign-in logs. This will give us a broad understanding of who is using basic auth, today I often see service accounts using basic auth for some application.
- Go to aad.portal.azure.com
- Go to Azure Active Directory
- Go to Sign-in logs
- Select client app (legacy authentication) and Application contains "Office 365 Exchange online)
Tip: change date to more than 24 hours.
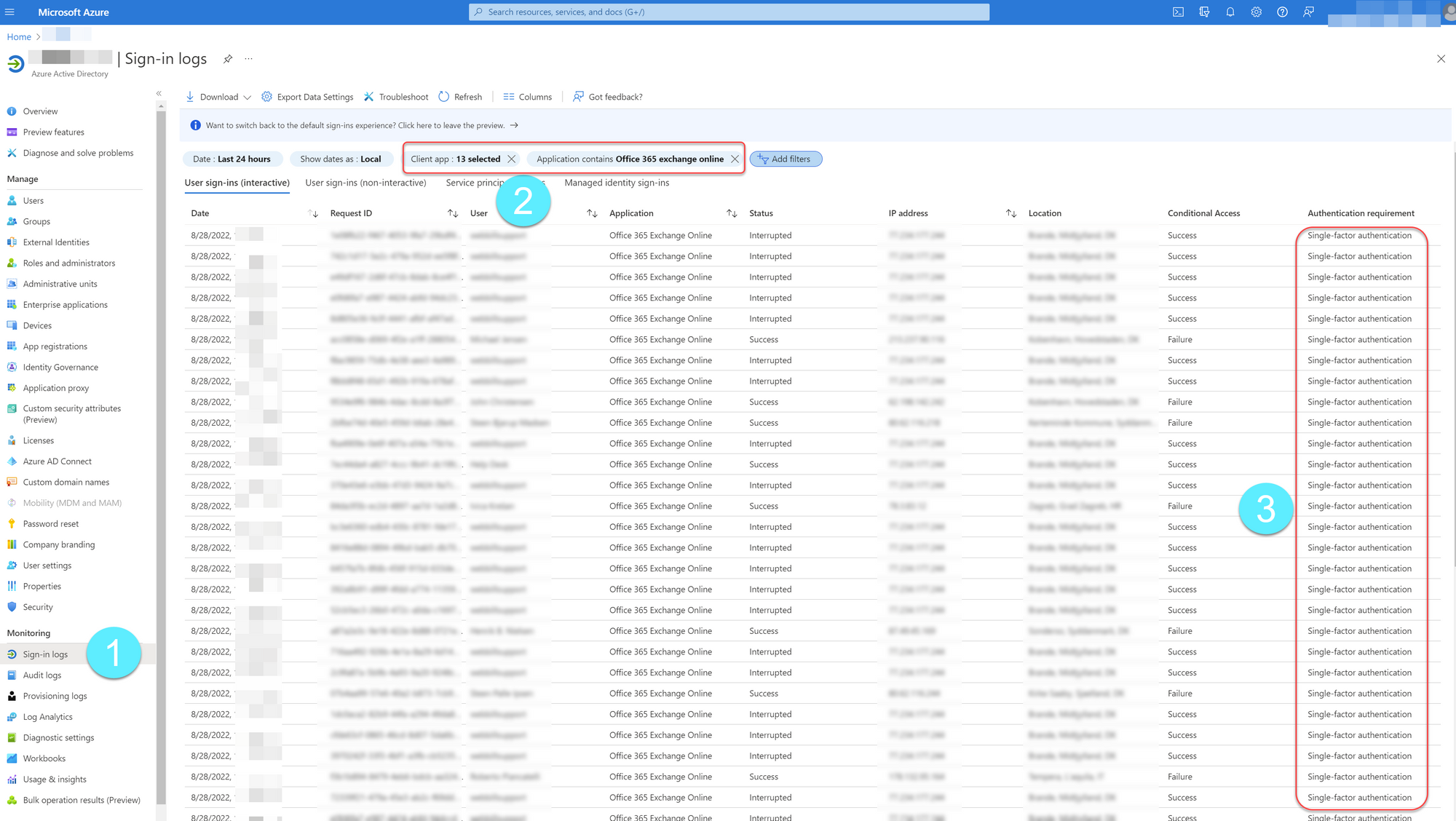
If we observe sign-ins to EXO using legacy auth (single-factor authentication), we should set EXO to report-only and determine the number of users who are actually logging in with only a username and password. Next, it would be blocked for a small number of users on each platform, so you can observe the transition to Modern Auth (Multi-factor Authentication).
If there are no legacy auth (single-factor authentication) sign-ins to EXO, we can create a CA policy that blocks all legacy authentication to EXO.
- Go to Security
- Go to Conditional access
- Click new policy
Please be knowledgeable if you plan to disable legacy authentication for EXO.
I'm not a fan of focusing solely on blocking Exchange Online Basic Authentication when such an important topic as basic auth is at hand; you might as well gain a deeper understanding of your environment now that you have the opportunity to do so. However, as our deadline is rapidly approaching, we will prioritize blocking Exchange Online Basic Authentication.
Next will be policy configuration.
How to block Basic Auth for Exchange Online
Users or workload identities = Include Test group
Cloud Apps = Exchange Online
Conditions = Client apps = Configure = Yes = Select "EAS and Other clients"
Grant = Block Access
Enable policy = On or Report only
Create the policy
Report only
Conditional Access policy state called "report-only mode" enables administrators to assess the effects of Conditional Access policies prior to enabling them in their environment.
Follow this Microsoft guide if you believe a better understanding is required.

More information




