
Use case: Phishing resistant MFA of a privileged role
Table of Contents
It's been a while since I've had a chance to update my blog! Between juggling work commitments and trying to carve out some free time, this year has really kept me on my toes as a freelance consultant.
I recently had the opportunity to speak at Expert Live, focusing on Privileged Identity Management (PIM) and password security. Inspired by that session, this post dives into a practical use case for protecting privileged roles in Microsoft Entra Identity Governance, specifically through Entra Identity Governance P2. We'll explore how leveraging Conditional Access, Authentication Strength, and Authentication Context can fortify our front gatekeepers.
Protecting Privileged Roles
Prioritizing the protection of privileged roles is a must in today's security landscape. If you haven't begun, now's the time to start.
Through technical implementations I've encountered, organizations often deploy Conditional Access to enforce protections based on certain conditions, such as location, coupled with Password Plus (Password+) protection. Password+ requires a second verification step after the correct password is entered, a security measure many organizations have adopted. However, as the sophistication of authentication security evolves, so too must our approach to safeguarding privileged roles.
Understanding Authentication Strength
Authentication Strength is all about the robustness of the verification mechanisms in place for accessing resources. It's not just about having a password or a second factor; it's about how those elements can withstand attempts at unauthorized access. By defining different levels of authentication strength within Entra Identity Governance, organizations can tailor the security requirements for accessing sensitive systems or data, ensuring that only users who meet these stringent criteria can proceed.
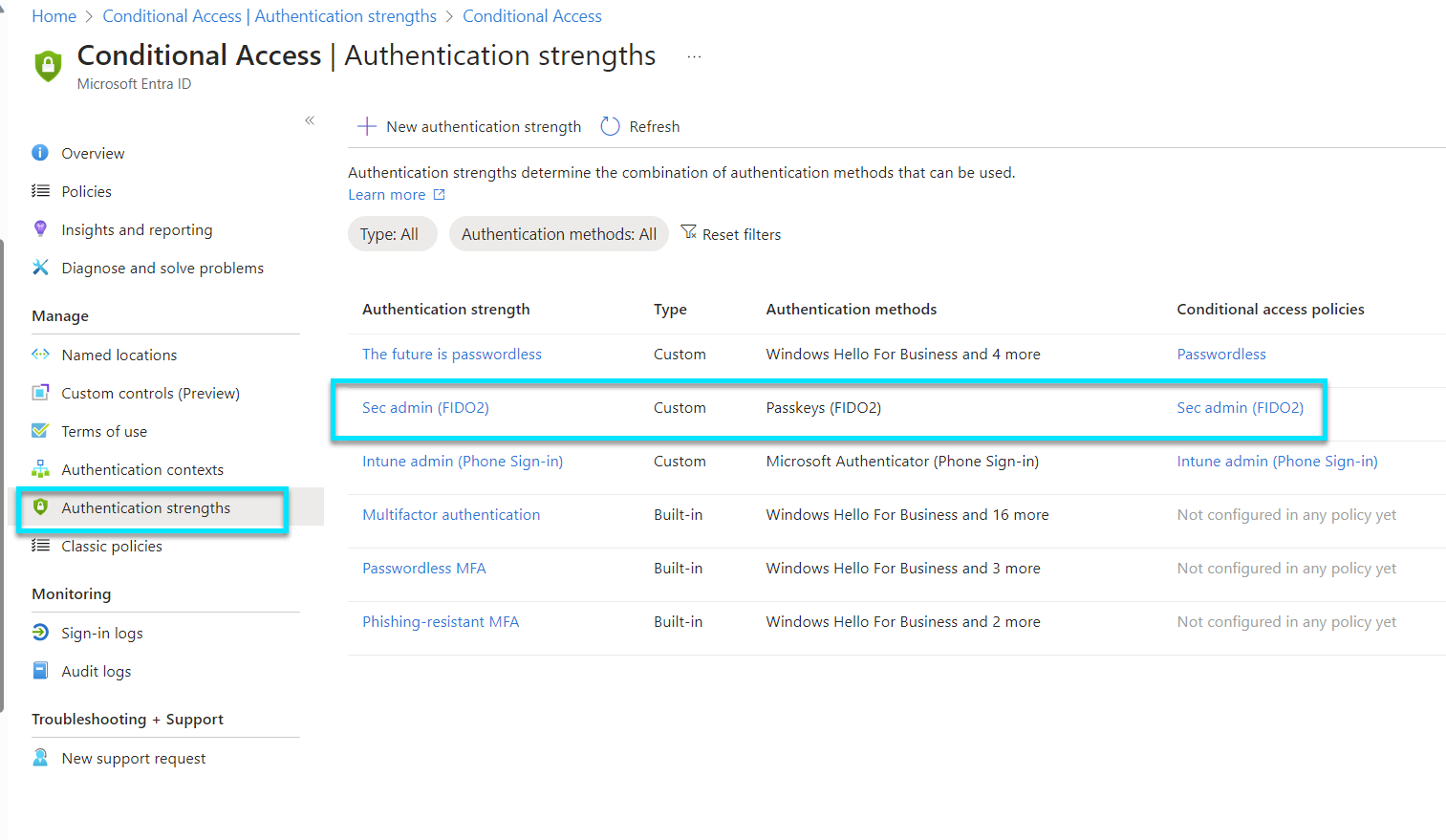
Here we are going to the use Passkeys (FIDO2) to accomplish phishing resistant MFA.
Leveraging Authentication Context
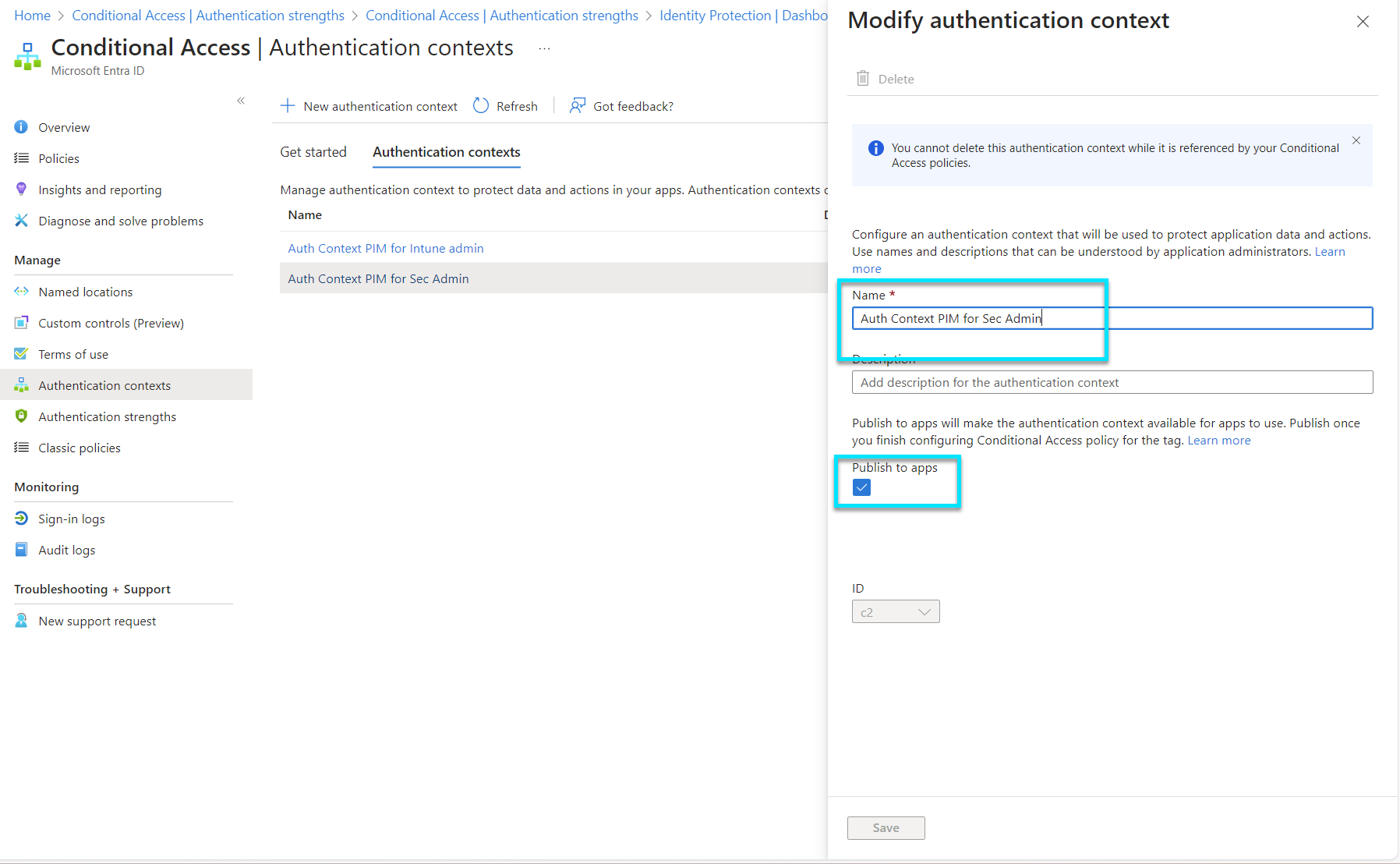
Authentication Context allows for the specification of different levels of authentication based on the sensitivity of the data or application being accessed. It adds another layer of granularity to Conditional Access policies, enabling organizations to require stronger authentication methods for more sensitive actions, further reducing the attack surface for privileged roles.
The Role of Conditional Access
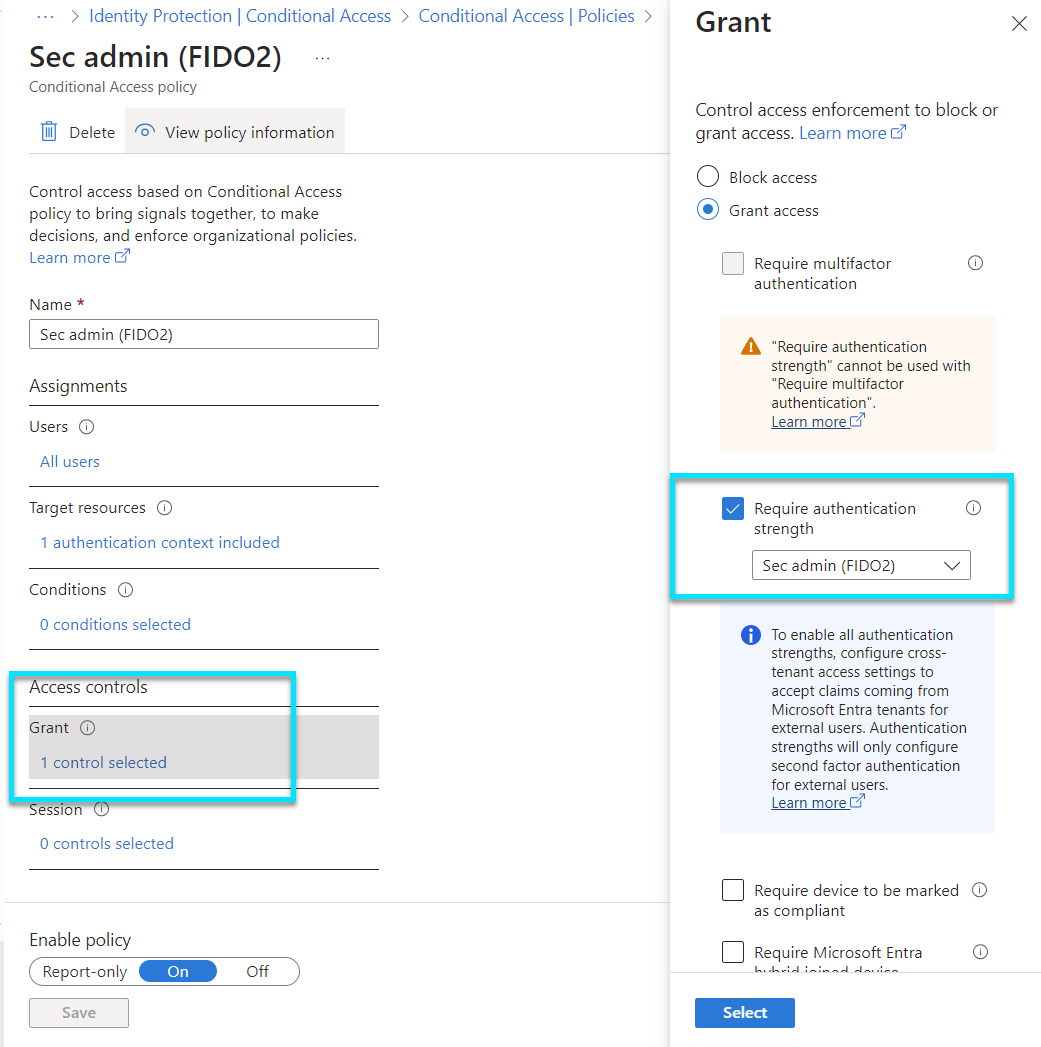
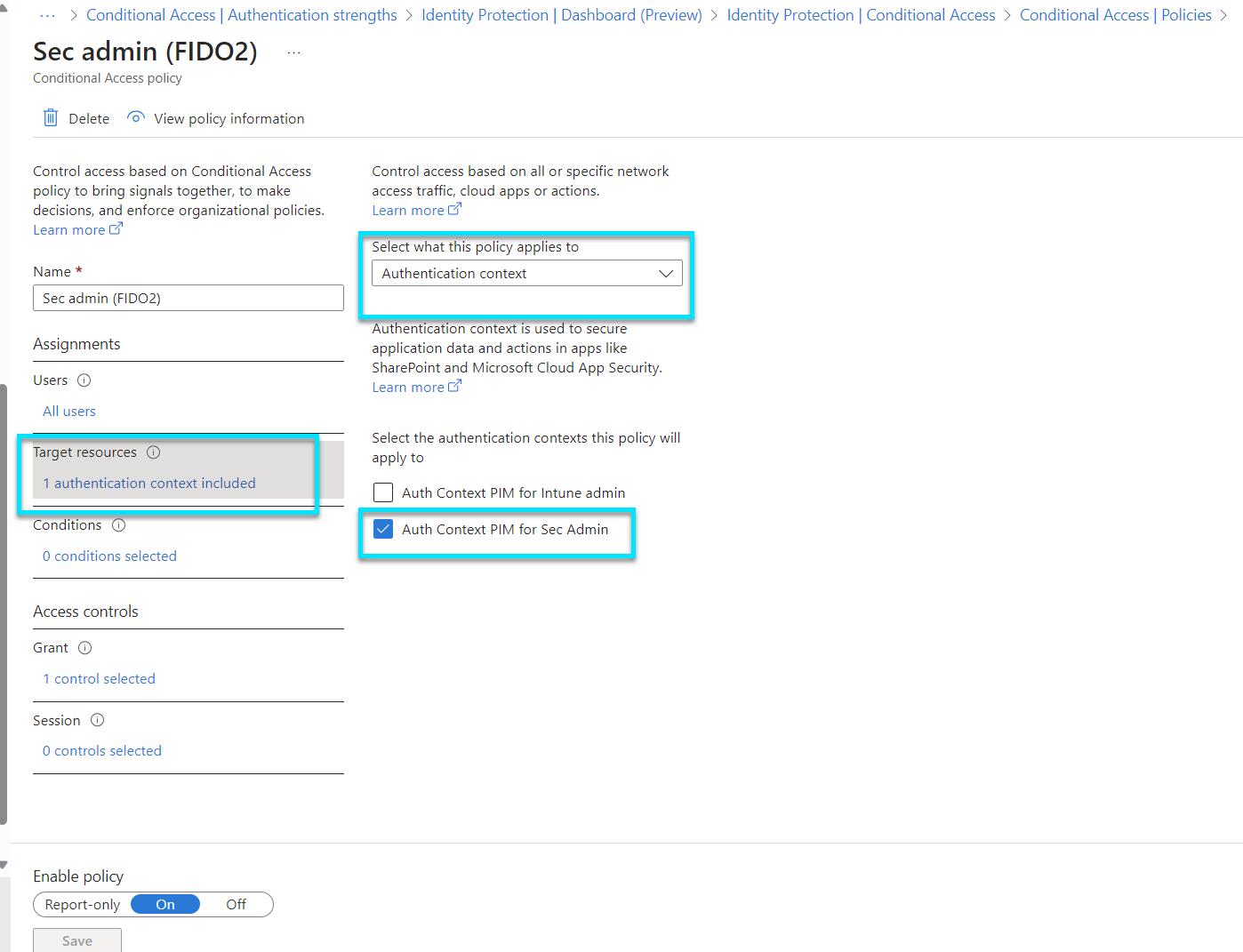
Conditional Access acts as a gatekeeper for your organization's applications and data, applying the right access controls under the right conditions. It's a policy-based approach that evaluates the context of access attempts, like the user's location, the device they're using, or the app they're trying to access. Based on these conditions, it determines whether to grant access, require additional authentication, or block access altogether. It's a powerful tool for minimizing risk while enabling productivity from anywhere.
Privileged Identity Management (PIM)
PIM is a critical component in managing, controlling, and monitoring access within an organization, especially for roles with elevated privileges. It helps minimize risks by ensuring that access to privileged roles is only granted when needed, for a limited time, and under strict supervision. This approach not only enhances security but also helps in meeting compliance requirements by providing detailed access logs and reports.
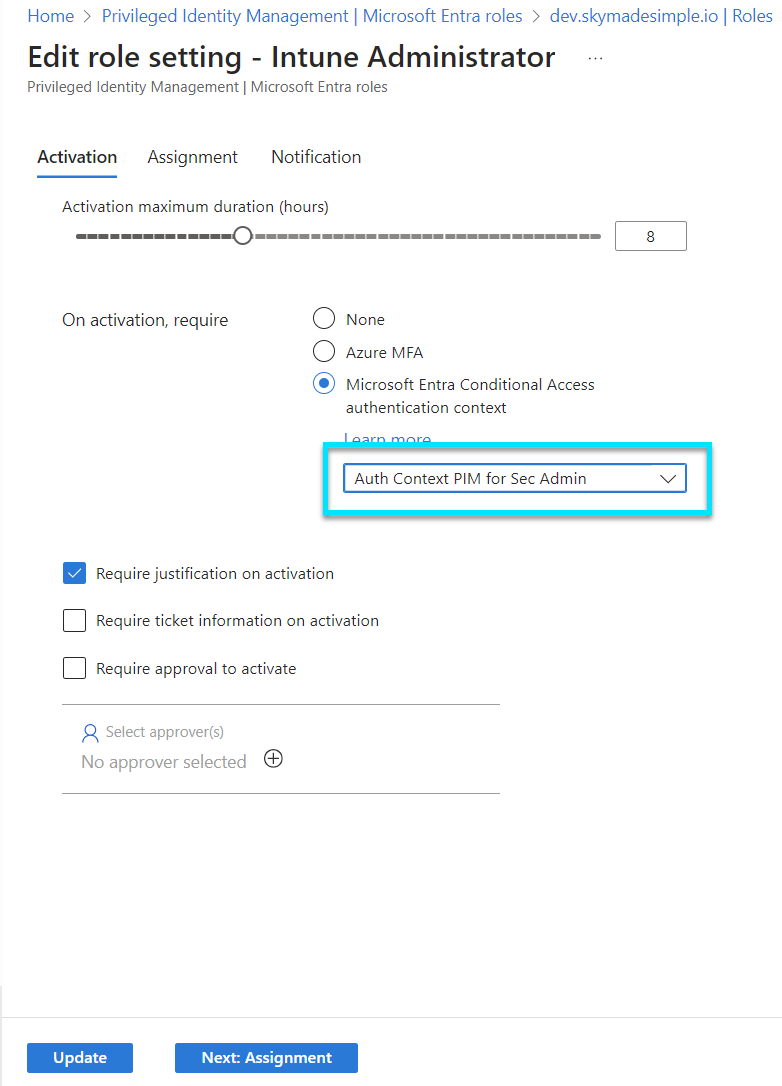
Bringing It All Together
Now, let's see how these components work together to elevate the security of privileged identities. Imagine a scenario where a privileged role attempts to access a highly sensitive system. With Entra Identity Governance P2, we can set up Conditional Access policies that assess the context of the request, enforce an appropriate authentication strength based on the sensitivity of the action, and apply specific Authentication Context requirements for this access attempt. In this case activating Intune Administrator role.
By integrating these solutions, we create a multi-layered defense strategy that adapts to the complexity of modern threats, ensuring that our privileged identities are protected with the highest standards of security.


