
The Mysterious Life of PRT: The Beginning
Table of Contents
Welcome to the first part of my new series, "The Mysterious Life of PRT: The Beginning". In this series, we'll journey into the world of Primary Refresh Tokens (PRT), exploring their role in modern authentication protocols across multiple platforms.

From Windows to macOS, from Android to iOS, we will peel back the layers of complexity that often shroud our understanding of these crucial elements in the authentication process. We'll delve into how different platforms manage user credentials, handle encryption keys, run system integrity checks, and more.
For those who might be new to this, a Primary Refresh Token (PRT) is an essential component of authentication on all these platforms. It's used in Azure AD authenticated apps for Single Sign-On (SSO), and how it's stored and managed differs from one platform to another.
Whether you're an IT professional wanting to deepen your understanding, a software developer looking to build more secure applications, or simply a curious tech enthusiast, this series will shed light on the often-overlooked but vital aspect of our digital lives - the mysterious life of PRTs.
I'd like to give a special shoutout to Michael H for inspiring the title "The Mysterious Life of PRT." Hes idea added an extra touch of intrigue to this blog post, and I am truly grateful. Thank you, Michael!
The Beginning
It began with my recent LinkedIn post, which gained traction and made me realize that there are likely others who also want to unravel the mystery alongside me.
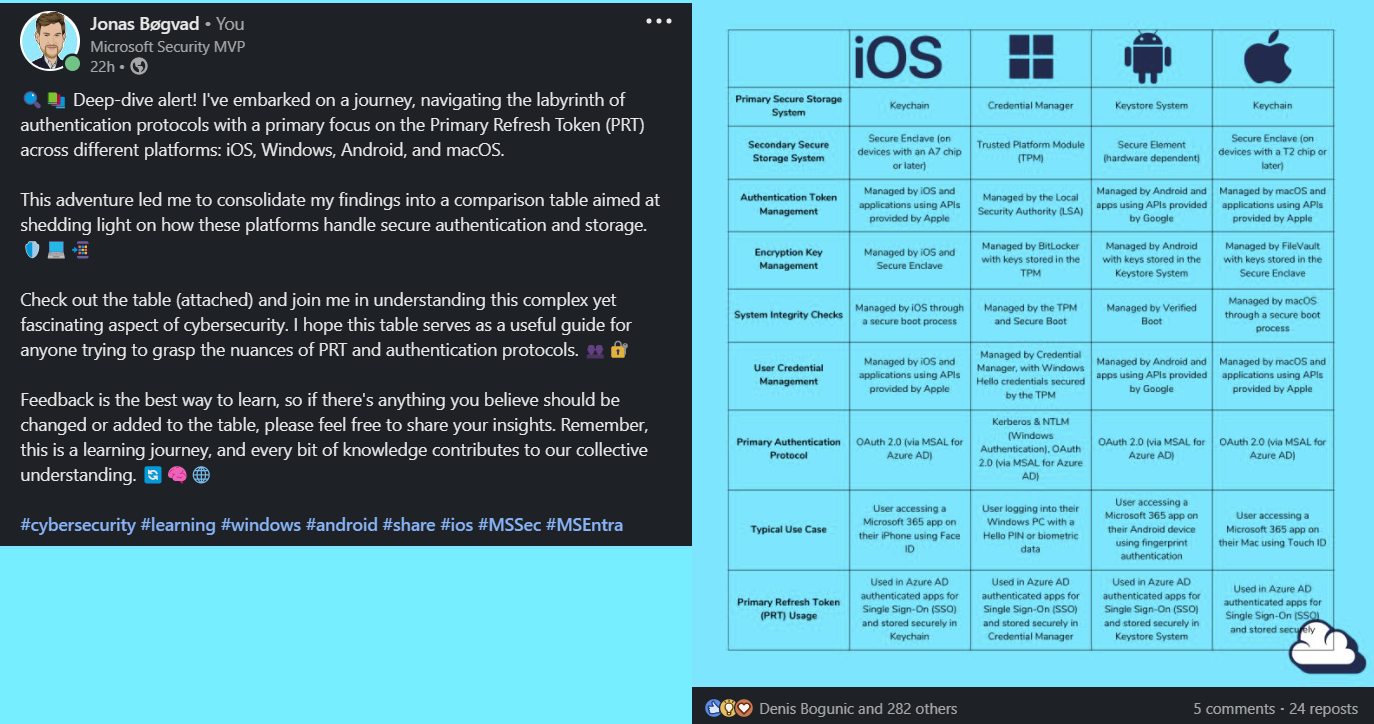
The table on the right side caught people's attention and sparked engagement with my LinkedIn post. This post is just the beginning, and I hope to share more like it in the future.

A Cryptic Glimpse into Each Platform
Enjoy the updated table, which now includes a description of each row and column. Use it however you see fit for educational purposes.
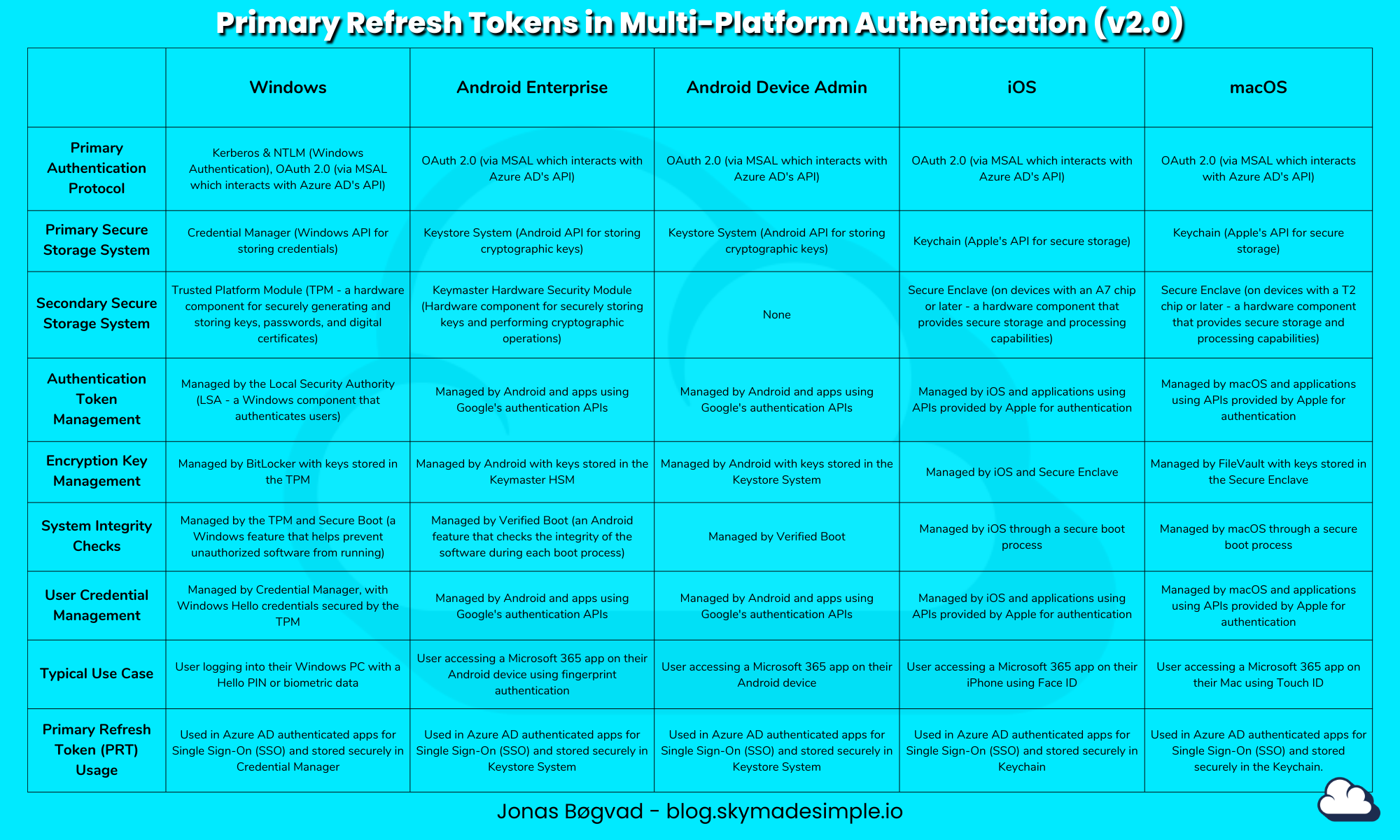
Primary Authentication Protocol
The Primary Authentication Protocol sets the foundation for user identity verification in a system. This protocol is the first step in establishing a user's identity to ensure secure access to resources.
- Windows: Windows uses a combination of Kerberos & NTLM (Windows Authentication), and OAuth 2.0 (via MSAL for Azure AD) as its primary authentication protocols.
- Android Enterprise: Android Enterprise relies on OAuth 2.0, with Azure AD interactions handled via MSAL.
- Android Device Admin: Like Android Enterprise, Android Device Admin uses OAuth 2.0 for authentication, with Azure AD interactions managed via MSAL.
- iOS: iOS also relies on OAuth 2.0 for authentication, with Azure AD interactions managed via MSAL.
- macOS: macOS, like its iOS counterpart, uses OAuth 2.0 for authentication, with Azure AD interactions handled via MSAL.
User Credential Management
User Credential Management involves the process of storing, managing, and securing user credentials such as passwords and digital certificates.
- Windows: In Windows, the Credential Manager handles user credential management, with Windows Hello credentials secured by the TPM.
- Android Enterprise: Android Enterprise manages user credentials and associated APIs provided by Google.
- Android Device Admin: Android Device Admin, like Android Enterprise, manages user credentials using APIs provided by Google.
- iOS: iOS manages user credentials and the associated APIs provided by Apple.
- macOS: macOS manages user credentials and the associated APIs provided by Apple.
Authentication Token Management
Authentication token management is the process by which tokens, representing verified user identities, are generated, distributed, and monitored. The way these tokens are managed is crucial to maintaining secure and efficient access to resources.
- Windows: The Local Security Authority (LSA) in Windows is responsible for managing authentication tokens.
- Android Enterprise: Android Enterprise manages authentication tokens by utilizing APIs provided by Google.
- Android Device Admin: Android Device Admin manages authentication tokens in a similar manner as Android Enterprise, using APIs provided by Google.
- iOS: For iOS, authentication tokens are managed by the operating system and applications using APIs provided by Apple.
- macOS: macOS follows a similar approach as iOS, managing authentication tokens through the operating system and applications using Apple-provided APIs.
Primary Secure Storage System
The primary secure storage system is the main repository for storing sensitive data, including passwords and encryption keys. It is designed to keep this information safe from unauthorized access.
- Windows: On Windows, the Credential Manager serves as the primary secure storage system.
- Android Enterprise: For Android Enterprise, the Keystore System acts as the primary secure storage system.
- Android Device Admin: Like Android Enterprise, Android Device Admin utilizes the Keystore System as the primary secure storage system.
- iOS: Apple's iOS uses Keychain as the primary secure storage system.
- macOS: macOS, like iOS, utilizes Keychain as the primary secure storage system.
Secondary Secure Storage System
The secondary secure storage system provides an additional layer of security for sensitive data. Often implemented as a hardware solution, it delivers extra protection against physical attacks or system compromises.
- Windows: Windows uses the Trusted Platform Module (TPM) as its secondary secure storage system.
- Android Enterprise: The secondary secure storage system for Android Enterprise includes Keymaster and Secure Element, but availability can depend on the specific hardware of the device.
- Android Device Admin: Unlike Android Enterprise, Android Device Admin does not have a secondary secure storage system.
- iOS: iOS uses Secure Enclave as its secondary secure storage system, but it is only available on devices with an A7 chip or later.
- macOS: macOS also utilizes Secure Enclave as its secondary secure storage system, available on devices with a T2 chip or later.
Encryption Key Management
Encryption key management is a critical aspect of data security that involves the creation, storage, distribution, and deletion of encryption keys.
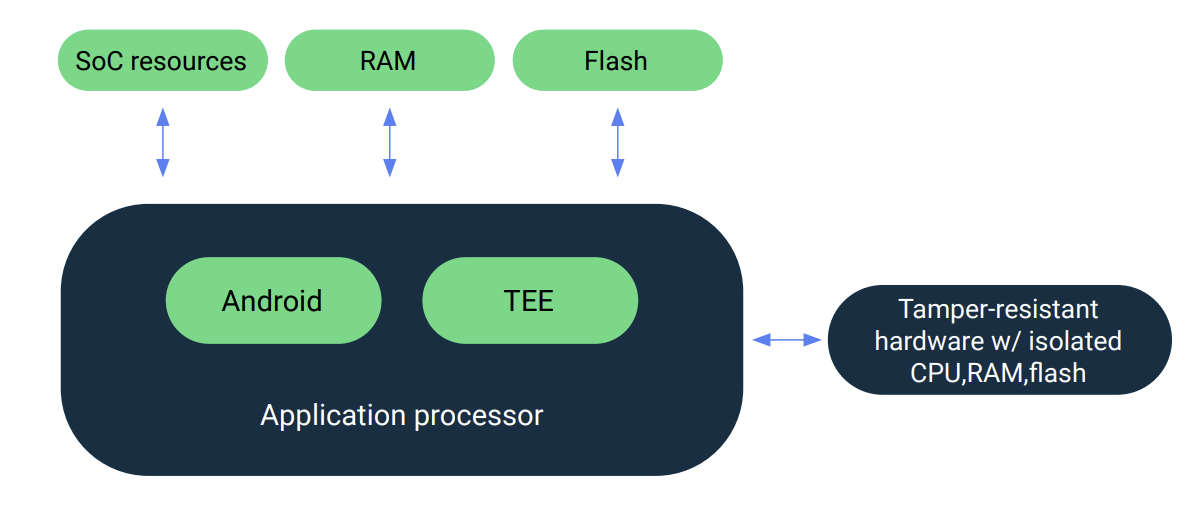
- Windows: On Windows, BitLocker manages the encryption keys, which are stored in the TPM.
- Android Enterprise: Android Enterprise manages the encryption keys, which are stored in the Keymaster and Secure Element.
- Android Device Admin: Android Device Admin manages encryption keys, which are stored in the Keystore System.
- iOS: iOS, along with Secure Enclave, manages the encryption keys.
- macOS: FileVault, together with Secure Enclave, manages the encryption keys on macOS.
System Integrity Checks
System integrity checks are security measures designed to ensure the integrity of the system by detecting unauthorized changes.
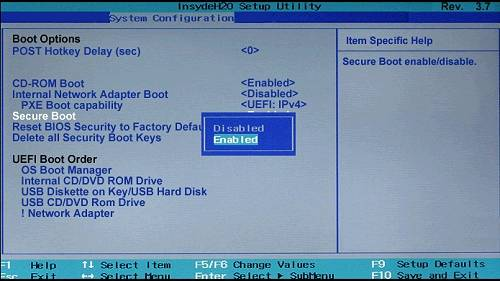
- Windows: On Windows, the TPM and Secure Boot manage system integrity checks.
- Android Enterprise: Android Enterprise uses Verified Boot for system integrity checks.
- Android Device Admin: Android Device Admin also utilizes Verified Boot for system integrity checks.
- iOS: iOS performs system integrity checks through a secure boot process.
- macOS: Like iOS, macOS also performs system integrity checks through a secure boot process.
Typical Use Case
The typical use case describes a common scenario where the features and capabilities of the platform are utilized.
- Windows: A typical use case for Windows involves a user logging into their Windows PC using a Hello PIN or biometric data.
- Android Enterprise: On Android Enterprise, a common use case might involve a user accessing a Microsoft 365 app on their device using fingerprint authentication.
- Android Device Admin: A typical use case for Android Device Admin is similar to Android Enterprise, with a user accessing a Microsoft 365 app on their device.
- iOS: On iOS, a typical use case could involve a user accessing a Microsoft 365 app on their iPhone using Face ID.
- macOS: A typical use case on macOS might involve a user accessing a Microsoft 365 app on their Mac using Touch ID.
Primary Refresh Token (PRT) Usage
Primary Refresh Token (PRT) is a key artifact of Azure AD authentication, enabling Single Sign-On (SSO) across applications.
- Windows: In Windows, PRT is used in Azure AD authenticated apps for SSO and is stored securely in the Credential Manager.
- Android Enterprise: For Android Enterprise, PRT is used in Azure AD authenticated apps for SSO and is stored securely in the Keystore System.
- Android Device Admin: Like Android Enterprise, Android Device Admin also uses PRT.


