
Latest updates on Microsoft Entra at Microsoft Ignite
Table of Contents
This post will drill down the session about Microsoft Entra. Keeping up with the latest happenings at Microsoft Ignite is challenging, so I've focused on a single session that directly relate to my interest, which lie within the Microsoft Entra and Security.
Microsoft Entra consist of 4 topics.
- Azure Active Directory
- Microsoft Entra Permission Management
- Microsoft Entra Verified ID
- Microsoft Entra Identity Governance
- Microsoft Entra Workload Identities 🆕
The new portal which includes everything Microsoft Entra, can be found at Entra.microsoft.com.
There has been both positive and negative changes recently, just see this twitter post regarding product renaming. A group name facilitates membership, not memory. Perhaps a future post will address group names and best practices.
I shouldn't have used MEM as a Groupname prefix.
— Martin Schmidli (@martin_schmidli) October 12, 2022
I shouldn't have used MEM as a Groupname prefix.
I shouldn't have used MEM as a Groupname prefix.#MEM #Intune #MEMnomore #Ignite #Ignite2022
I know how he feels, but don't get your teams used to brand names because the changes you're making will likely last.
What's new in Microsoft Entra
Microsoft Entra is a universe for identity and access management that controls and validates all of your identities across machines and users.
- Machine identity (workload identity)
- Human identity (user identity)
Certificate-based Authentication
Microsoft Entra in Azure Active Directory now includes Certificate-based Authentication which satisfy specific use cases and specially the blocker of migration away from ADFS.

Multi-factor authentication Phishing resistant in Azure Active Directory
Phishing-resistant MFA is multi-factor authentication (MFA) that is immune from attempts to compromise or subvert the authentication process, commonly achieved through phishing attacks, which includes but is not limited to spear phishing, brute force attacks, man-in-the-middle attacks, replay attacks and credential stuffing. Uses FIDO standard and Windows Hello for Business
It is suggested you assign if...
- Targeted executives
- Access to sensitive data
- NOT All users⚠️
Microsoft Entra Identity Governance
Microsoft Entra Identity Governance helps businesses give the right people access to the right resources at the right time. This update will provide full-featured identity governance for local and cloud-based identity provider.
Microsoft Entra Identity Governance simplifies operations, consolidates identity point solutions, and supports regulatory compliance.
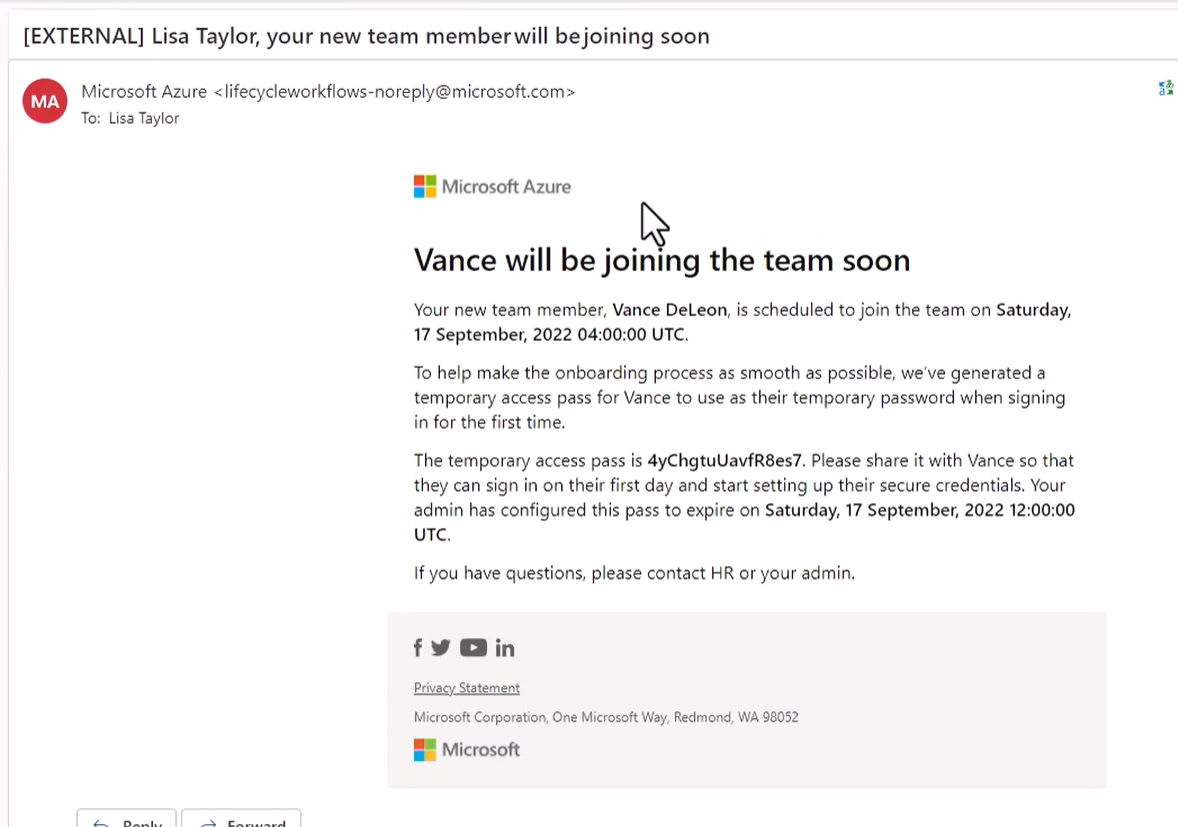
Microsoft Entra Workload Identities
Workload identity is referred to as both an machine identity and a new service within Microsoft Entra. The service's goal is to ensure that we are managing our Workload identities or machine identities and to return control to us.
Workload identity is a new umbrella term which leverage none human actions.
- Application
- Service Principal
- Managed Identity
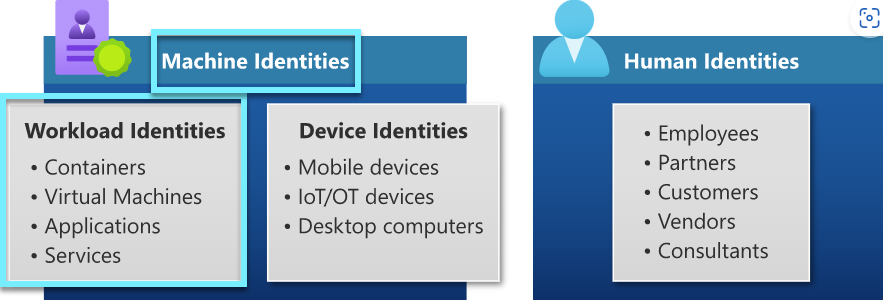
By "workload identities," Microsoft particularly refers to non-human identity features linked with the use of apps and services, which can include things like containers and virtual machines.

Workload identities are currently unmanaged and therefore insecure, but they have far greater access than the average user. Machine identities (workload identities) have a 5:1 advantage over human identities. (will only rise rapidly)
Workload Identity is an identity and access management solution that will be available to everyone in November 2022. It will manage the identity lifecycle for digital workloads such as apps and services, as well as access to cloud resources.
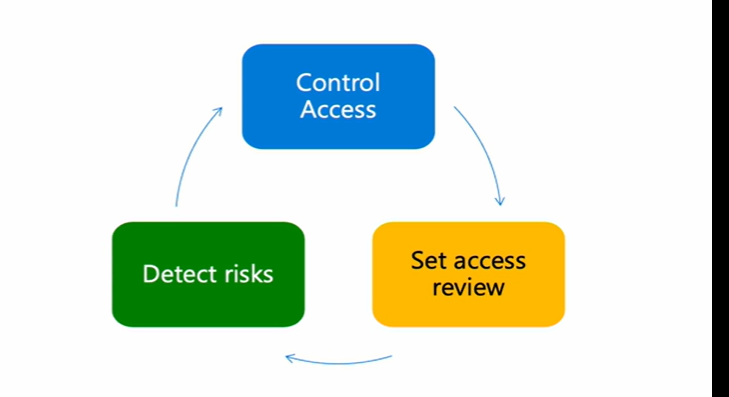
What you can now
We can now use Conditional Access to make policies based on risk, Identity Protection to find and protect workload identities, and Access Reviews to make sure that only the least-privileged people can access workload identities.
- Review service principals and applications that are assigned to privileged directory roles in Azure AD using access reviews for service principals.
- Access Azure AD protected resources without needing to manage secrets (for supported scenarios) using workload identity federation.
- Apply Conditional Access policies to service principals owned by your organization using Conditional Access for workload identities.
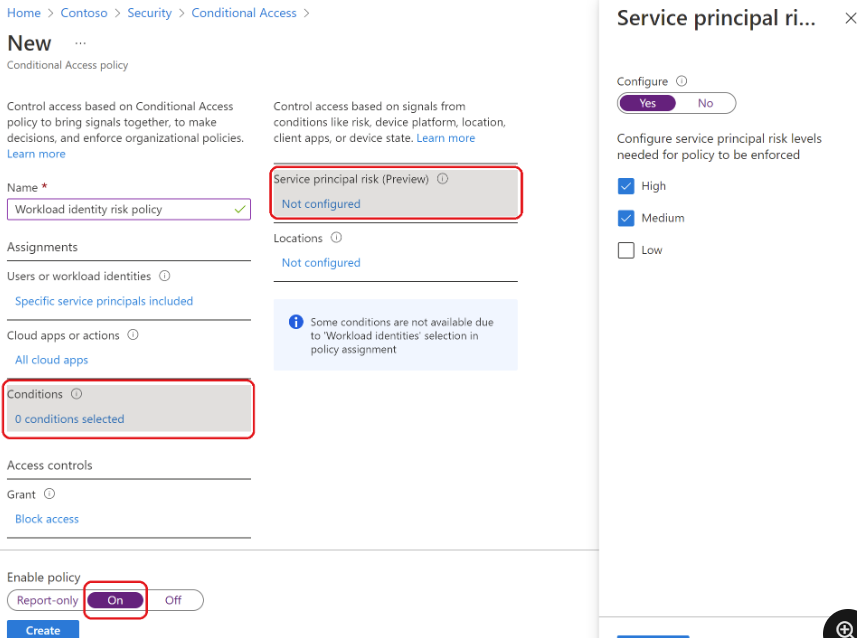
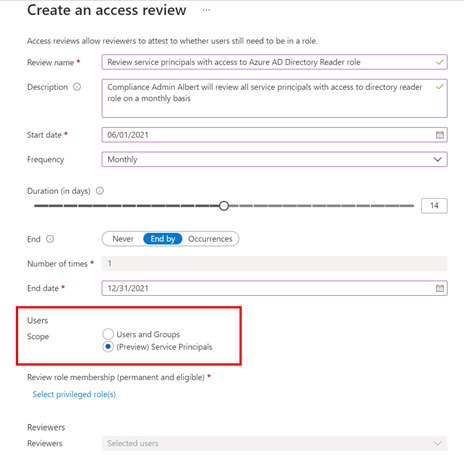
You can see the new possibilities with Workload identity in this video.
More Information
Twitter spaces from Microsoft focusing on Identity
Folks we have FIVE 🚀 #MSIgnite Azure AD Twitter Spaces coming up this week with various Microsoft PMs!
— Merill Fernando (@merill) October 10, 2022
I have added all of them to the thread below.
Click ‘Set Reminder’ to be notified when the session starts so you can join us live@markmorow @BaileyBercik
🧵👇🏾
1/6







