
Microsoft 365 Defender with learning paths🔐
Table of Contents
Let's get an overview of each Microsoft 365 Defender service
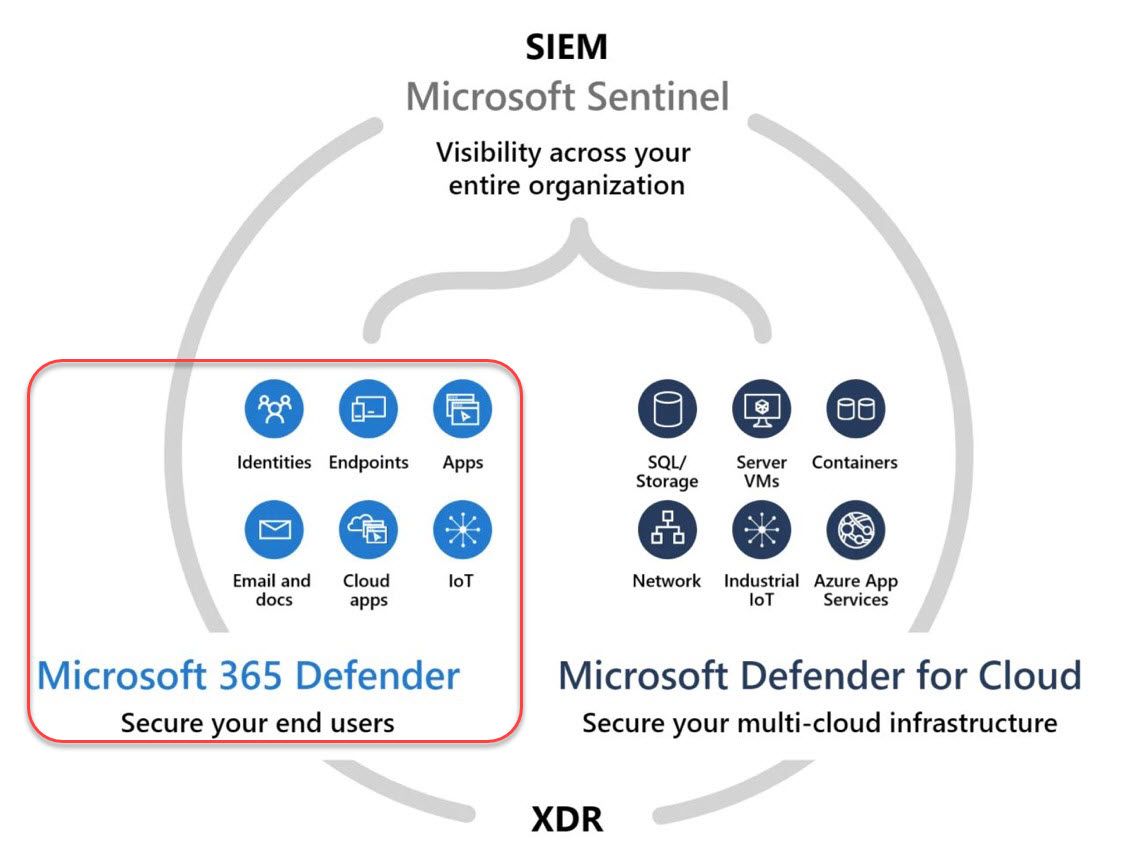
Microsoft 365 Defender services
M365 Defender is a comprehensive enterprise security suite that safeguards endpoints, identities, email, and applications. Each service is incorporated into the modern workplace and is an important participant in the security landscape, especially if you already have M365 services like AD DS, Azure AD, Sharepoint, Onedrive, Teams, Exchange, and so on.
What are you waiting for? Let's get started!
For the entire 365 experience, each service requires some configuration and onboarding.
💻Microsoft Defender for Endpoint
Do you want to protect your Endpoints with a unified platform built on the latest technology? Defender for Endpoint uses the newest Endpoint Detection Response method, which destroys traditional Anti-virus scans on any benchmark. A single Endpoint Security solution can protect each Endpoint in our environment. As of now, Microsoft supports almost any Operation System💯
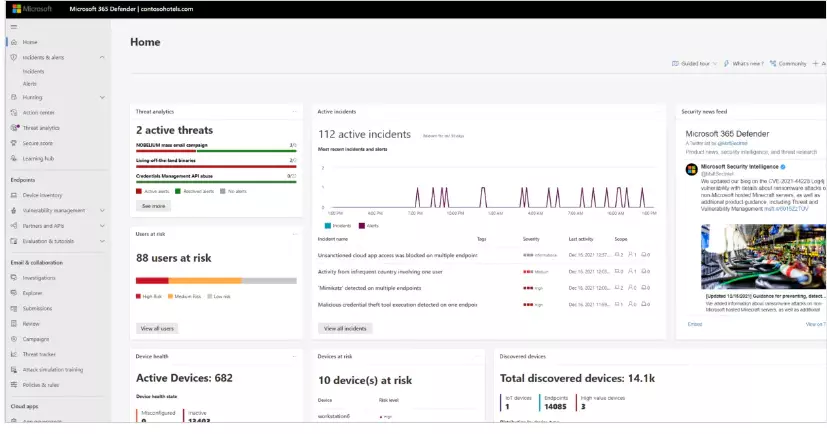
Vulnerability Management
As a security expert, you must be aware of your vulnerabilities on every Endpoint. You receive a TVM assessment report that outlines the vulnerabilities you should focus on.
- Continuous vulnerability and configuration finding
- Prioritization based on business context and dynamic threat landscape
- Correlation of vulnerabilities with endpoint detection and response (EDR) alerts to expose breach insights
- Machine-level vulnerability context during incident investigations
- Built-in remediation processes through a unique integration with Microsoft Endpoint Manager
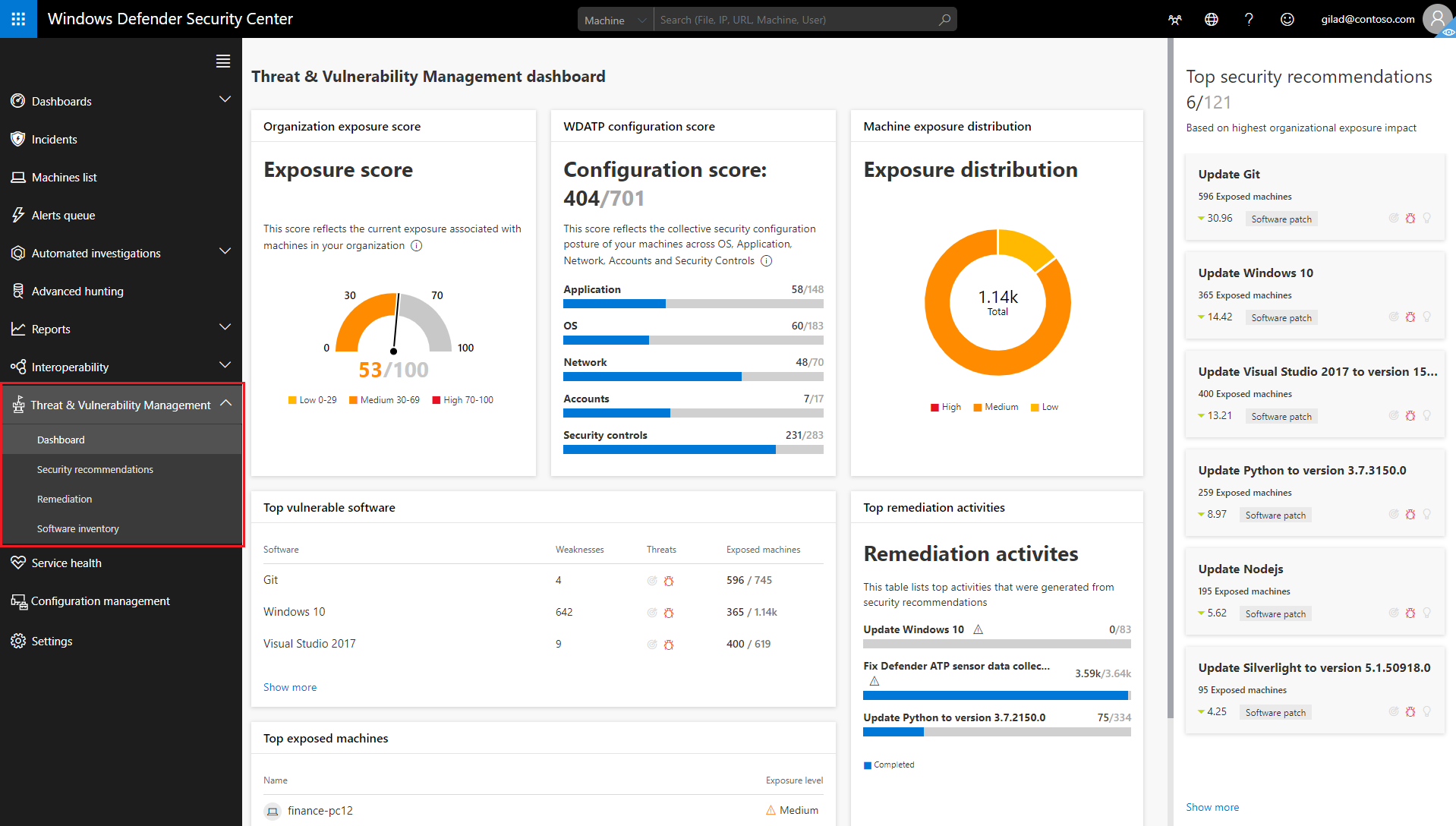
Learn Microsoft Defender for Endpoint

🆔Microsoft Defender for Identity
We must safeguard our estate if you utilize on-premises Active Directory Domain Services (AD DS), which we almost certainly intend to do for valid cause. We can identify, detect, and investigate threats across all of your user identities on-premises with defender for identity.
Azure AD identity protection
Is Azure AD used in a hybrid or all-cloud environment? It's an obvious decision to enable identity protection. It will automate the discovery and remediation of identity-based vulnerabilities such as impossible travel and password exposures in your Azure AD cloud environment.
Learn Microsoft Defender for Identity

📂Microsoft Defender for office 365
Our emails must be routed through Exchange Online for Defender to protect Office 365. If we are in a hybrid identity state, I strongly advise transitioning to full Exchange online, rather than starting with Hybrid Exchange Online.
Email communications, phishing tactics, user education, links, and other channels will be protected.
Learn Microsoft Defender for office 365

🍎Microsoft Defender for Cloud Apps
By taking control of your cloud environment, you may improve your security posture. With Microsoft 365 Defender for Cloud Apps, a cloud access security broker (CASB) that gives comprehensive visibility, control over internet traffic, and powerful analytics, you can detect and combat cyber threats across all of your cloud services.
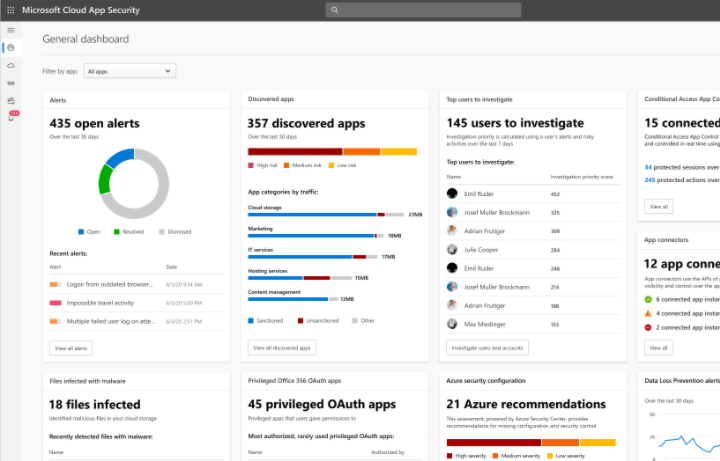
Learn Microsoft Defender for Cloud Apps

🖲️Microsoft Defender for IoT
Defender for Endpoint collaborates with Microsoft Defender for IoT to provide a comprehensive view of our device detection and agentless monitoring capabilities, which include IT networks, Voice over IP, printers, and cameras.
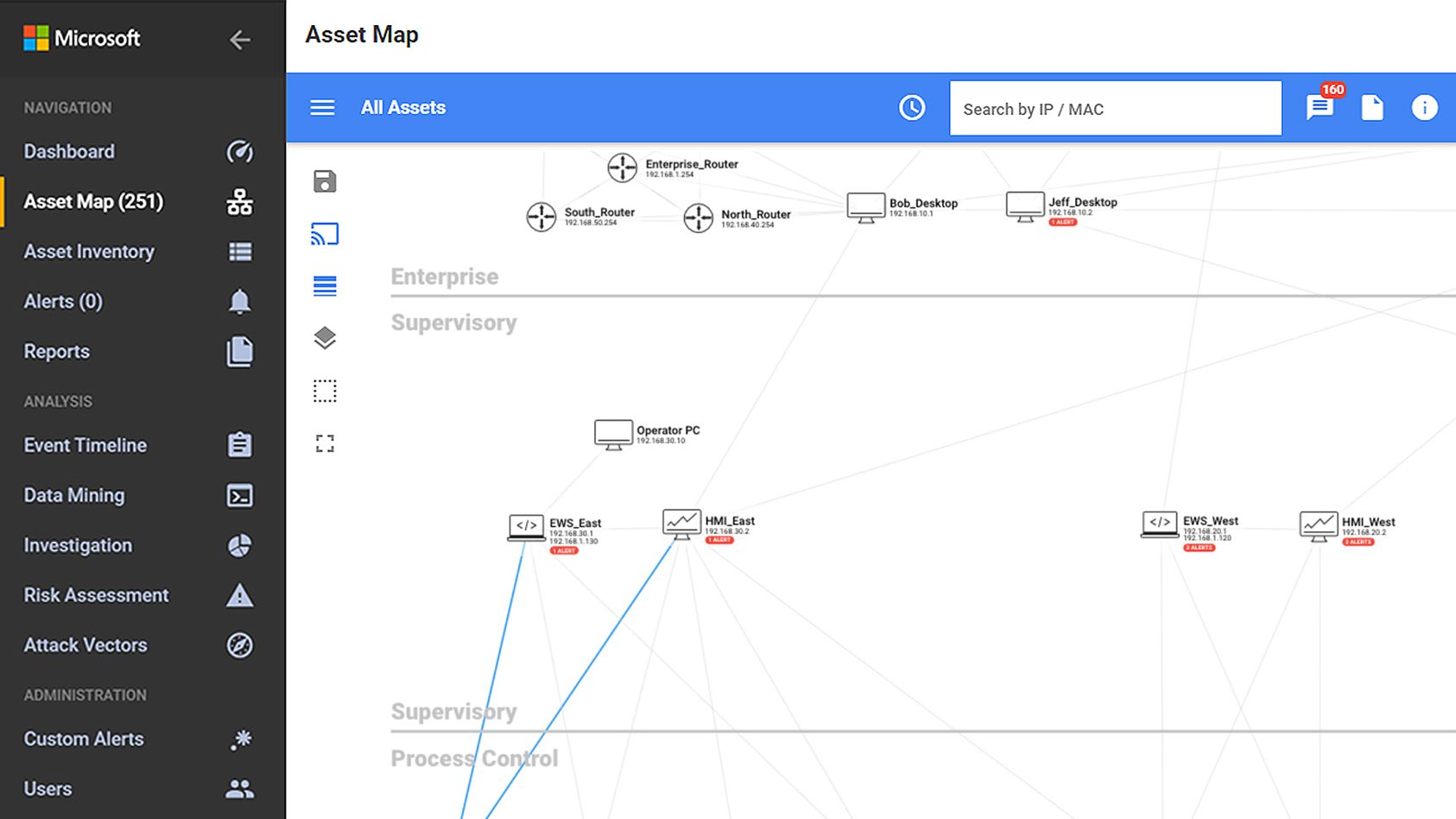
Learn Microsoft Defender for IoT

Ready to evaluate?

Licenses
If you own any of the following licenses, you may be able to use some of the features of security.microsoft.com depending on your licensing.
- Microsoft 365 E5 or A5
- Microsoft 365 E3 with the Microsoft 365 E5 Security add-on
- Microsoft 365 E3 with the Enterprise Mobility + Security E5 add-on
- Microsoft 365 A3 with the Microsoft 365 A5 Security add-on
- Windows 10 Enterprise E5 or A5
- Windows 11 Enterprise E5 or A5
- Enterprise Mobility + Security (EMS) E5 or A5
- Office 365 E5 or A5
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Defender for Office 365 (Plan 2)


