From warnings that don’t help to ones that do
Table of Contents
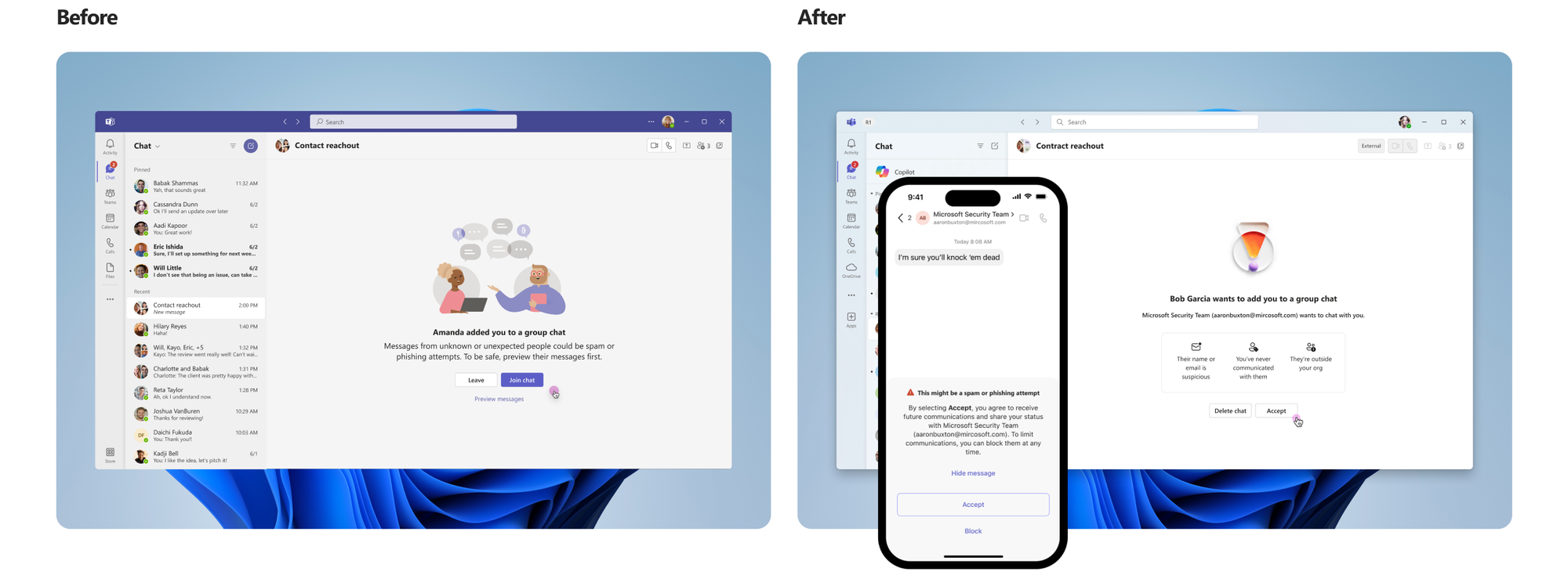
Imagine this: you get added to a group chat in Microsoft Teams.
You don’t know the person. You weren’t expecting the invite. But you click anyway. Why? Because the interface said something like:
“Messages from unknown people could be spam. You may want to preview them.”
That’s it. A high-risk moment, answered with a barely noticeable prompt.
Now fast forward to today. Same Teams, same scenario - completely different experience. This time, it says:
“Rob Garcia wants to add you to a group chat. Their name is suspicious. You’ve never communicated with them. They’re outside your org.”
Oh and it gives you three clear options: Accept, Delete chat, or Block.
That's not just a UI change. That’s security by design
Wait, haven’t we seen this concept before?
Actually, yes.
This idea stepping in only when it matters, with the right context has been part of Windows since UAC was introduced.
UAC prompts, as you know them, are Windows asking:
“Do you want to allow this app to make changes to your device?”
Except it doesn't scream. It doesn’t warn for the sake of warning. It steps in only when your action crosses a boundary something that changes system state or requires elevation.
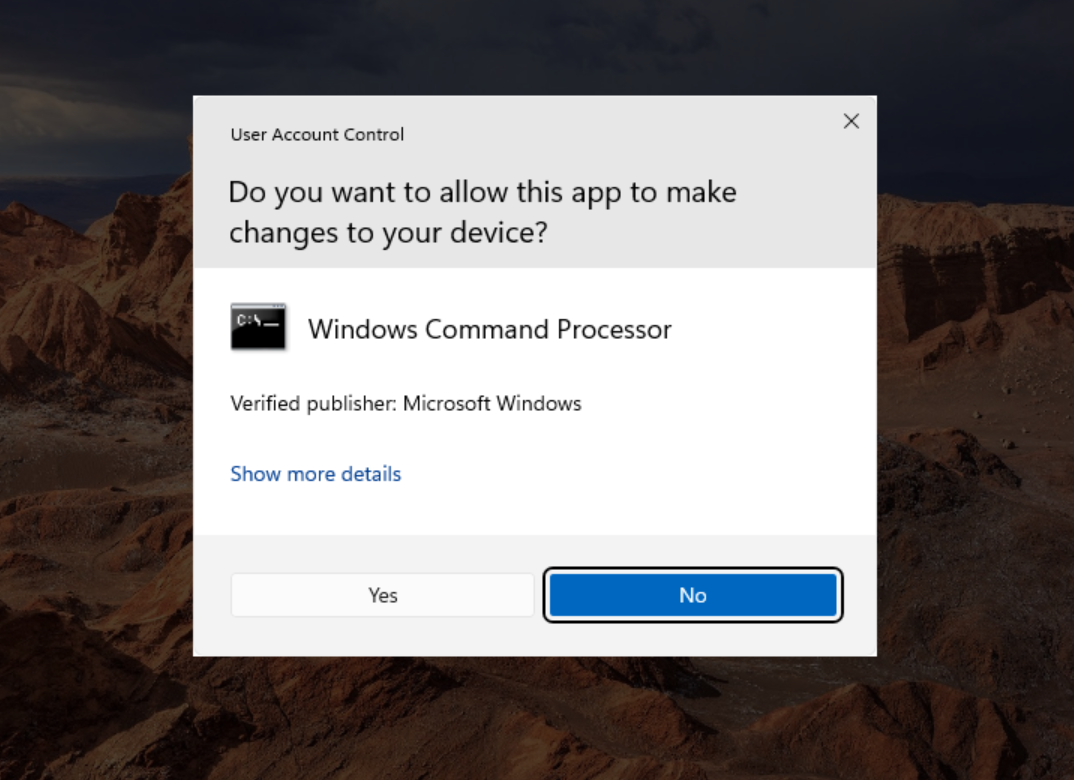
It teaches the user that something important is happening. And it gives them the power to decide with the guardrails still in place.
But what about us admins?
From an admin perspective, we’ve all been there.
Changing something in Conditional Access or Defender with your fingers crossed, thinking:
“Please don’t break sign-in for everyone.”
That experience? It’s getting smarter. Across Microsoft 365, admin portals are quietly shifting toward secure UX too just less visible to the outside world.
Conditional Access “What If” Simulation
When you build a new policy in Entra ID, you don’t have to guess anymore.
The "What If" tool shows who will be impacted before you hit save.
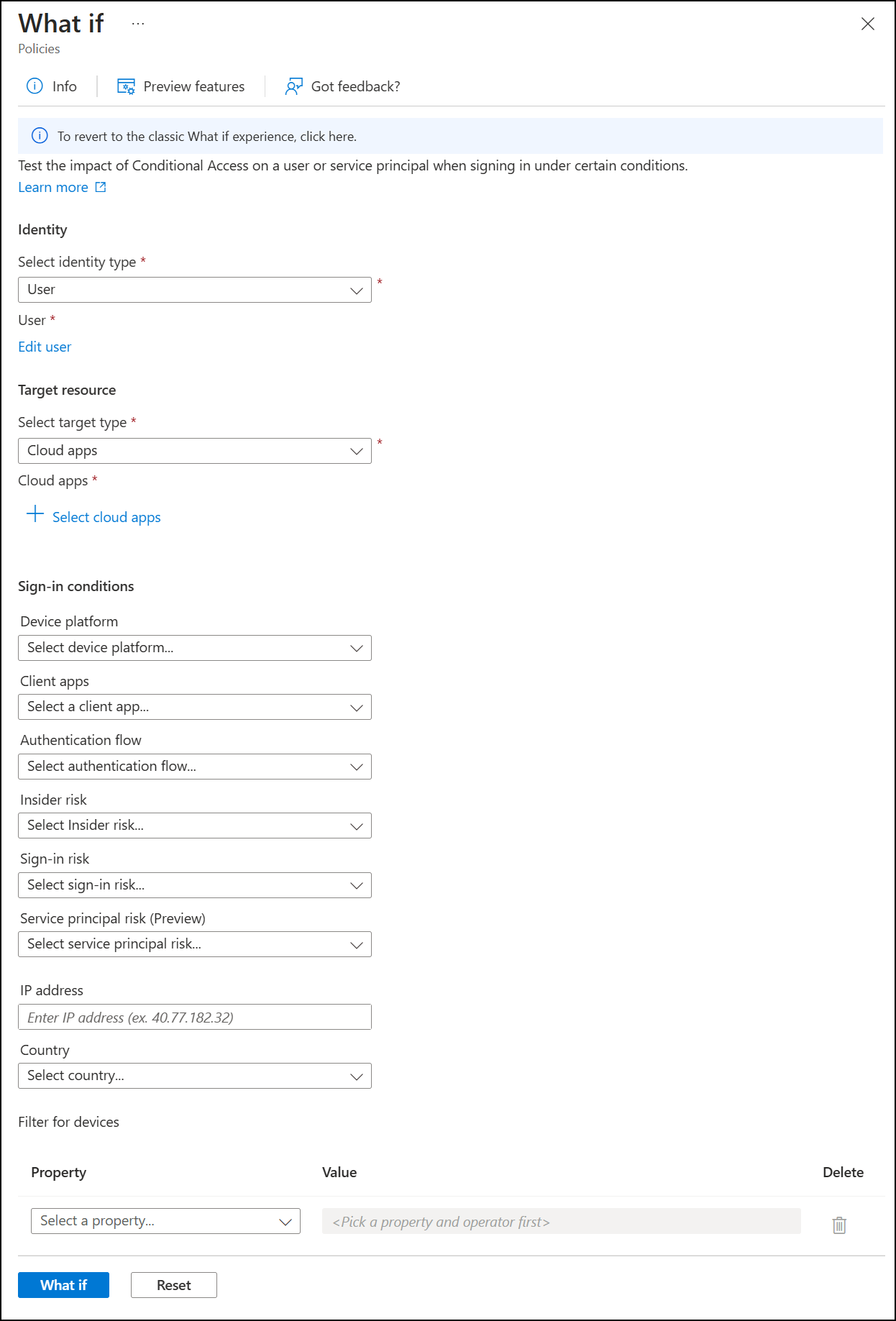
Simulation before impact. Because 9 AM on a Monday is not the time to find out you blocked the CEO.
Device Isolation
You get an alert. Time to isolate a device. But instead of jumping blind, Defender gives you context:
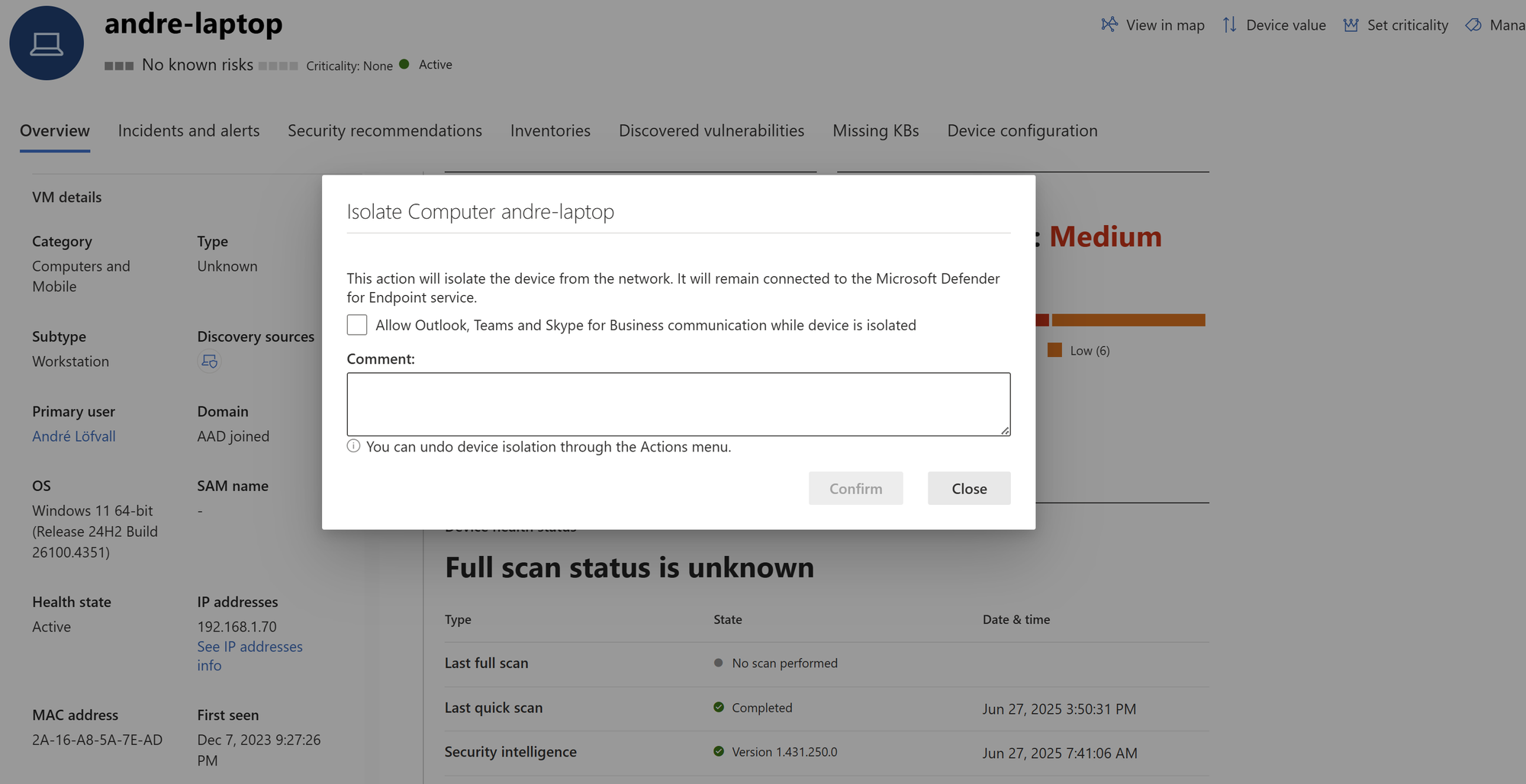
- What will actually happen
- An option to allow users to use M365 Apps (Currently new Teams is not supported)
- Add a comment, so you advice the rest of the team.
You still click isolate but now you do it with confidence.
More admin UX examples worth knowing
| Where | What it does | Why it matters |
|---|---|---|
| Microsoft Purview (DLP) | Shows policy impact before enforcing rules | Helps prevent accidental data exposure |
| Defender for Cloud Apps | Explains inline policy enforcement (e.g., upload block) | Teaches users the “why” in real-time |
| Microsoft Authenticator | Number matching and location info | Prevents MFA fatigue attacks |
It’s not about stopping users or admin.
Security by design isn’t about control. It’s about confidence.
Giving both users and admins just enough clarity to do the right thing at the right time with the right level of friction.
MitID has already proven this works at scale. Over 5 million Danes use strong, phishing-resistant login every single day and barely think about it.
So when someone says,
“We’re not ready for that.”
I say: if millions can handle secure UX every day so can your business.
Try this
Choose one flow in your organization:
- A risky login
- A user being phished
- An admin tweaking a high-stakes setting
Now ask yourself:
- Where’s the hesitation?
- Where are the blind spots?
- Could you surface context, timing, and choice better?
Ressource