
First evening on hack the box
Table of Contents
I've always felt the urge to try out Hack The Box, mainly to learn more about red teaming and get a firsthand look at how attackers operate. As many of you know, I’m a Microsoft MVP, working with security tools every day. Using these tools and knowing how to prevent attacks with them is crucial in cybersecurity. It's all about understanding the methods attackers might use and then fortifying defenses against them.
This blog post is not affiliated with or sponsored by Hack The Box. In fact, it was actually written back in August. Why did I wait? Because I thought it wouldn’t add much value. But let this be a lesson: if you find something interesting, share it. Just blog! You never know who might benefit from your insights and experience.
We know that somewhere, deep in the trenches, experts are developing and testing these tools before releasing them for businesses and individuals to use. This could be through companies like Microsoft or through open-source projects. Microsoft, for example, shares a lot of valuable security knowledge openly. But, let’s be real everything in this field is interconnected and often driven by business needs. Okay, small detour, let’s get back on track.
So, here’s the beginning of my Hack The Box journey.
Yep, we’re diving into the basics of penetration testing through one of their training modules. Why, you ask? Honestly, I ask myself the same question sometimes. But it comes down to wanting to understand what’s happening behind the scenes without getting too caught up in the typical tools and company jargon. Some might argue that AI will eventually take over, so why bother? I think it’s essential to understand the fundamentals of penetration testing and how these attacks actually work. Before you start using AI tools, you need to know where and why you're deploying them. This knowledge will give you a much broader perspective when discussing cybersecurity.
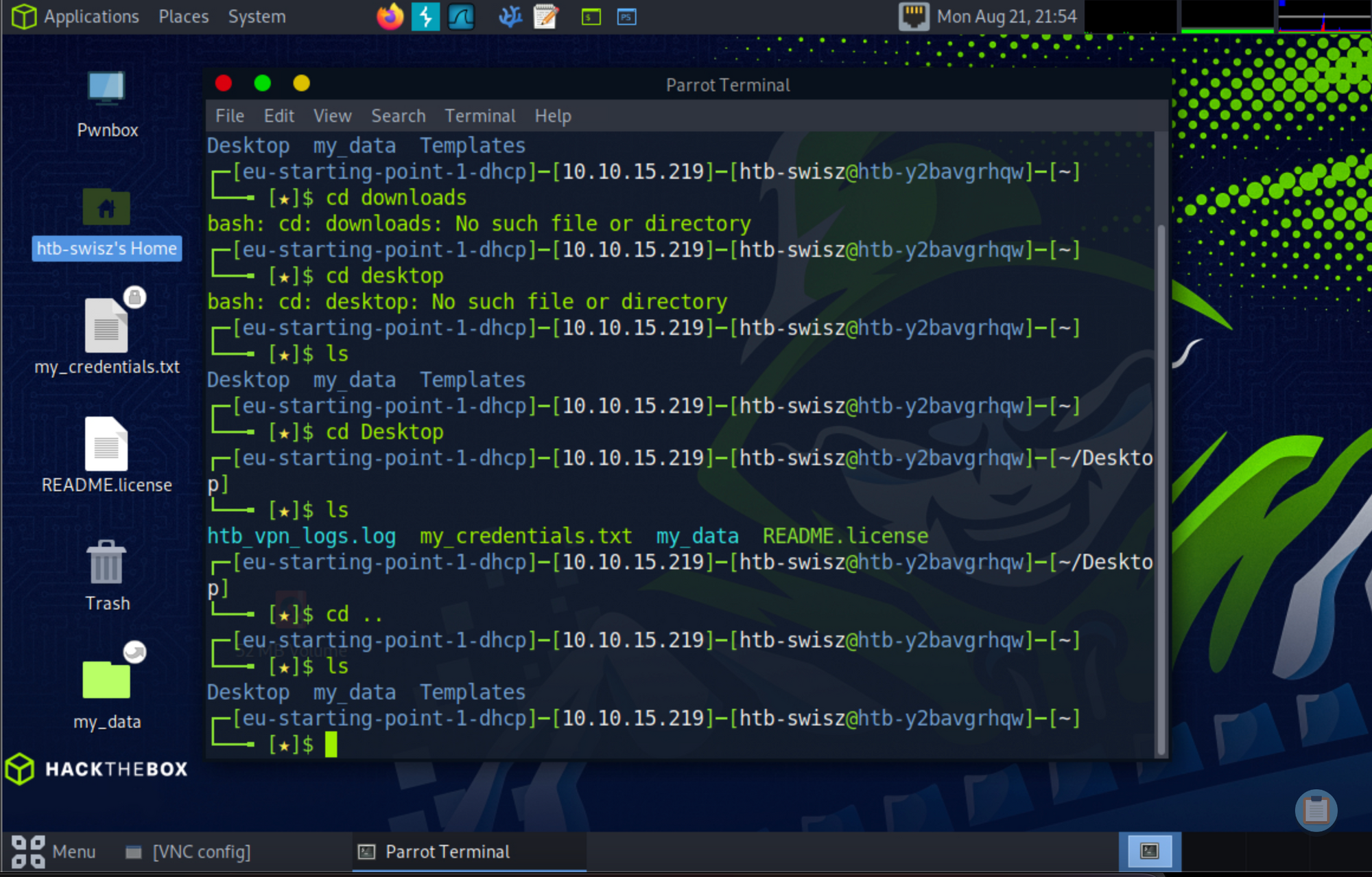
This blog post was inspired by the idea of stepping into the red team mindset and understanding how attackers approach a system especially as someone who usually works on the defense. It’s fascinating to think about the tools we use and develop daily from a different angle, with the mindset of a blue teamer learning from the other side. Test it out, if you find it interesting their testing environments are spot on!
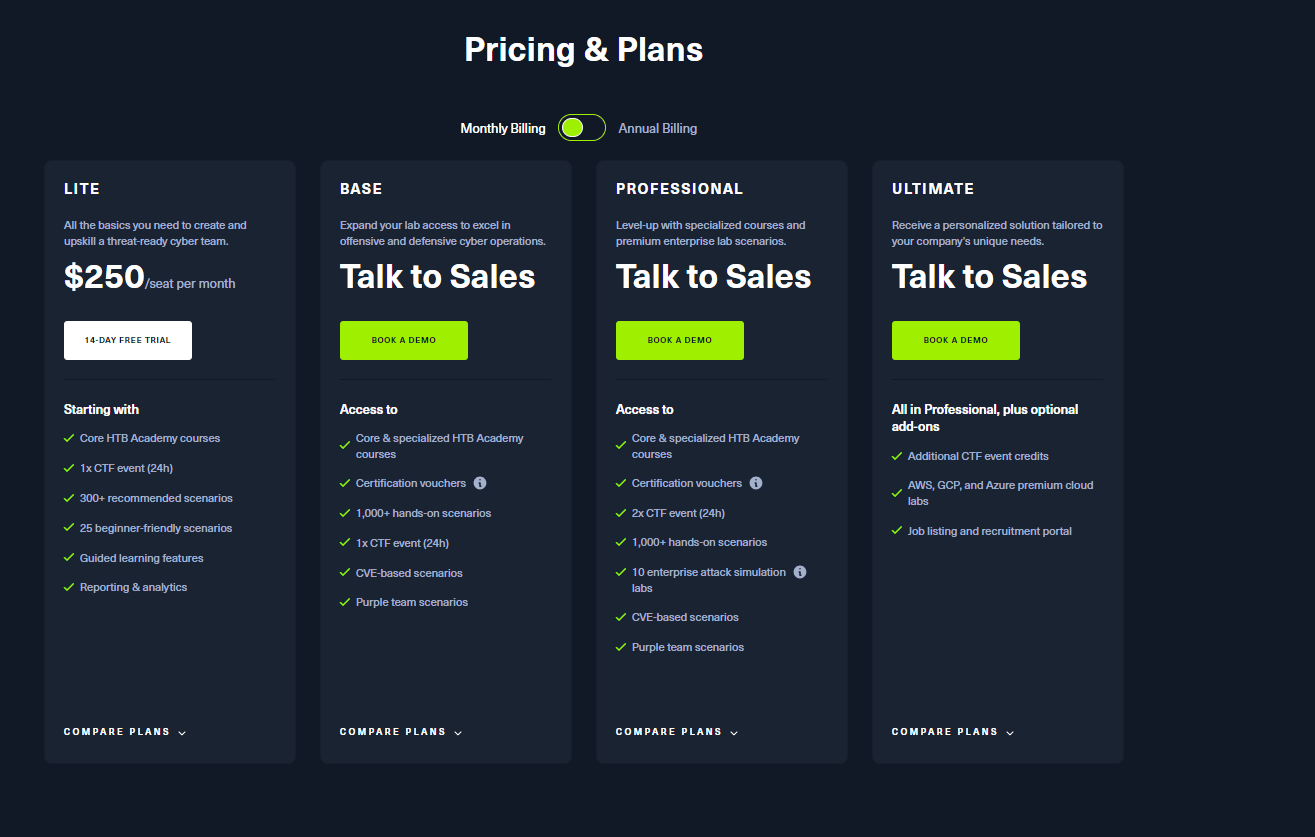
So, did I continue with testing? I did for a while and might pick it up again. But let’s be honest—the seat price is steep for a hobby pentester like me at "$250 per seat per month." I’d recommend looking into their "Academy Subscriptions" if you’re a student (which, unfortunately, I’m not on paper) or trying their 14-day trial before committing.
This wraps it up for now. If I continue, I’ll make sure to blog about it, balancing it with my work and my role in this awesome community. If you have any feedback, feel free to reach out on any of the channels where we’re connected.


