
Continuous Access Evaluation (CAE): The Silent Security Hero
Table of Contents
Ever Googled "Continuous Access Evaluation"? It's a term you may not encounter daily, but CAE plays an instrumental role in token security. Operating discreetly within systems, CAE is a mechanism that bolsters security in ways many aren't aware of.
Understanding Continuous Access Evaluation
Commonly referred to as CAE, Continuous Access Evaluation is a critical component of modern security protocols, particularly when it comes to token protection. It works quietly with Conditional Access but is very important.
Before the advent of CAE, clients replayed access tokens from their cache until they expired. Now, Microsoft's implementation of CAE allows for the initiation of a "claim challenge". This is a signal indicating token rejection, demanding the issuance of a new access token. Simplifying this concept: CAE enables real-time evaluation, eliminating the need to rely on static access token lifetime policies.
CAE enhances security by ensuring that access decisions are made based on the most recent and relevant information available. It reduces the window of opportunity for malicious actors to exploit valid tokens and ensures that access is always aligned with the current state of a user, their device, and their environment.
Key Innovations in Token Security
With the continuous evolution of security protocols, token security now includes:
- Critical Event Evaluation
- Conditional Access Policy Evaluation
- Token Protection for sign-in sessions (preview)
- Strict enforcement of Location Policies (preview)
These advancements significantly minimize delays between policy activations or revocations triggered by administrators. CAE's foundation lies in the "Continuous Access Evaluation Profile" by OpenID. Though many might not realize it, this backend structure is grounded in open standards. Microsoft even has a CAE API for you to integrate into your applications.
CAE in Action
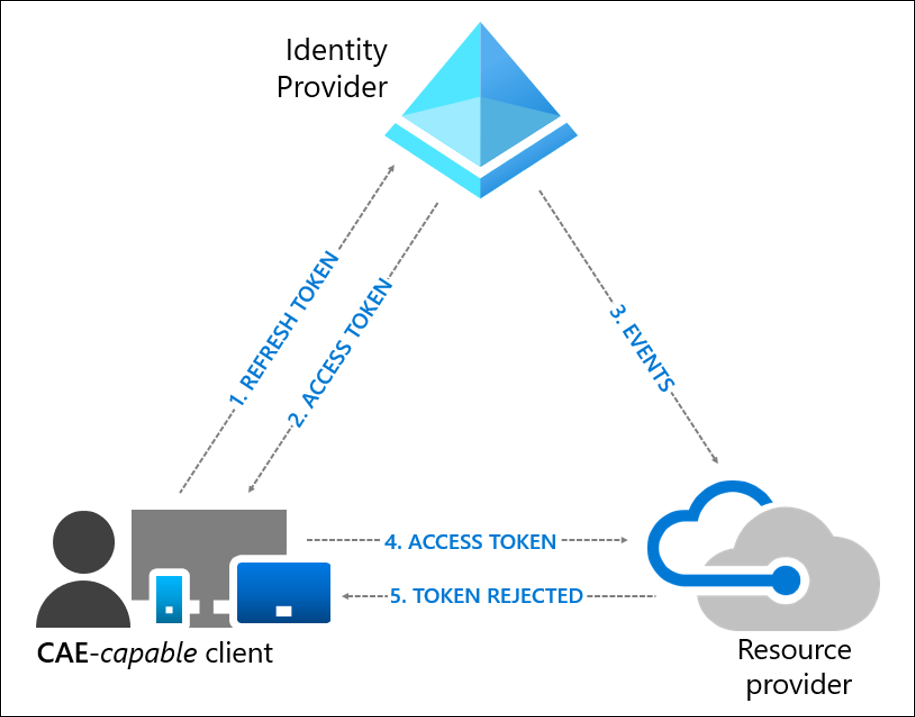
To understand Continuous Access Evaluation better, let's dive into its core components:
- Identity Provider: Manages user identities and is responsible for token issuance.
- CAE-capable client: Represents either a user or a system designed to operate with CAE.
- Resource Provider: A system or application accessed by the client. This system verifies token validity before granting access.
The CAE process is straightforward:
- Refresh Token: The client requests a new token from the Identity Provider using its refresh token.
- Access Token: The Identity Provider responds by granting an access token.
- Events: Significant events, be they user-oriented or administrative, are monitored by the Identity Provider.
- Access Token: The client, armed with this token, seeks access from the Resource Provider.
- Token Rejection & Client-side claim challenge: Traditional systems utilized cached access tokens till expiry. CAE shifts this paradigm. Resource Providers can reject non-expired tokens in light of significant events. A claim challenge then signals the client to bypass its cache, prompting it to fetch a new access token.
Modern Security frameworks

- Principle of Least Privilege (PoLP): CAE ensures that tokens can be revoked or modified in real-time, making sure that users have only the access they need at that specific moment. If a user's privileges change, CAE can reflect those changes immediately, adhering to the PoLP.
- Real-time Monitoring and Response: Most security frameworks emphasize the importance of real-time monitoring and response to potential threats. CAE allows for instant evaluation of token validity, meaning potential security breaches can be addressed in real time.
- Access Control: Dynamic access control is a hallmark of modern security frameworks. CAE, by constantly evaluating the validity of access tokens, ensures that only authenticated and authorized entities can access protected resources.
- Zero Trust Architecture: Zero Trust is a security concept centeret on the belief that organizations should not automatically trust anything inside or outside its perimeters. Instead, everything must be verified before granting access. CAE aligns with this by constantly re-evaluating tokens, not just relying on initial authentication.
- Auditability: With CAE, every token rejection or issuance based on an event is auditable. This is crucial for frameworks that require tracking of all access-related events for compliance.
- Standards Compliance: CAE is based on the Continuous Access Evaluation Profile by OpenID, a recognized standard. Adhering to recognized standards is often a key component of security frameworks.
- Integration with Other Systems: Modern security frameworks emphasize the importance of integrated security solutions. CAE, especially as implemented by Microsoft, can be integrated with other security solutions and systems, providing a holistic security posture.
- Data Protection and Privacy: By ensuring that only valid tokens can access resources, CAE plays a role in data protection, a critical aspect of many security frameworks.
In Conclusion
Continuous Access Evaluation stands as an unspoken hero in the domain of token security. As cloud systems evolve and security challenges mount, technologies like CAE will undoubtedly gain prominence. Microsoft is building its latest SASE solution around Conditional Access, which gain all the benefits of CAE's strength.
Resources



