
CIS Microsoft 365 Foundation Level 1 - Azure Active Directory
Table of Contents
Let me show you how to implement the CIS Microsoft 365 Foundation Level 1. We will focus on Azure AD and how to implement the controls.
Introduction to Center for Internet Security also known as CIS

CIS Microsoft 365 Foundation Level 1
The goal of the Microsoft 365 Foundations Benchmark is to help organizations set up a basic level of security for anyone who wants to use Microsoft 365. The benchmark is for system and application administrators, security experts, auditors, help desk and platform deployment staff who want to build, deploy, test, or secure solutions that use Microsoft 365.
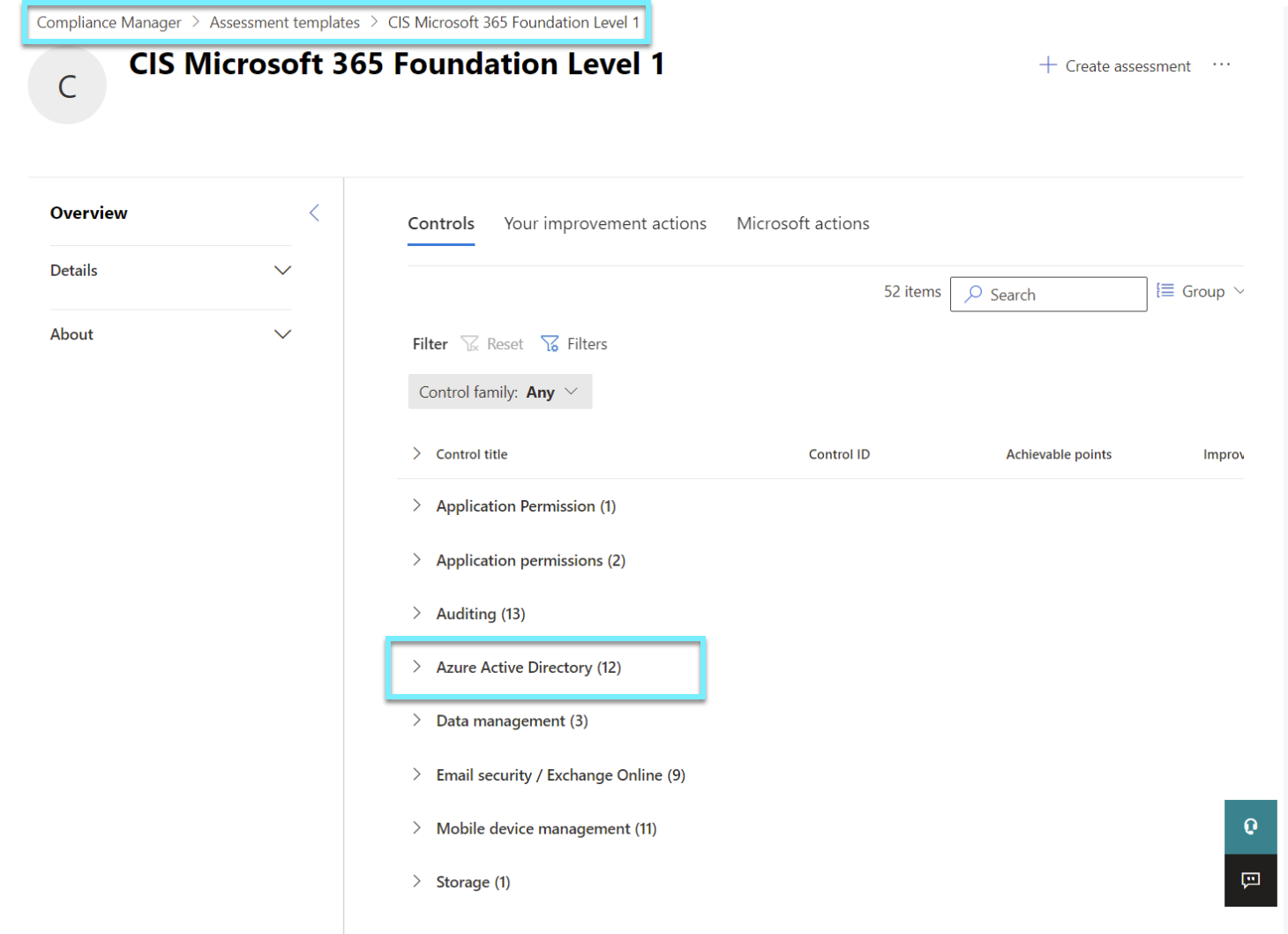
As we can see from the screenshot, the assessment template covers more than one Control title. I want to show you how Azure Active Directory and our identity work. Remember, everything you decide to implement should be done so with caution⚠️
Azure Active Directory Control titles
- Designate between two and four global administrators
- Enable conditional access policies to block legacy authentication
- Enabled identity protection to identify anomalous logon behavior
- Ensure modern authentication for Exchange Online, Sharepoint and Skype for Business is enabled (bundled)
- Ensure multifactor authentication is enabled for all users in administrative roles
- Ensure security defaults is disabled on Azure Active Directory
- Ensure self-service password reset is enabled
- Ensure that Office 365 passwords are not set to expire
- Ensure that password protection is enabled for Active Directory
Designate between two and four global administrators
Global Administrator also known as GA is the most powerful role and should only be given to a small number of accounts, like our Break the Glass account.
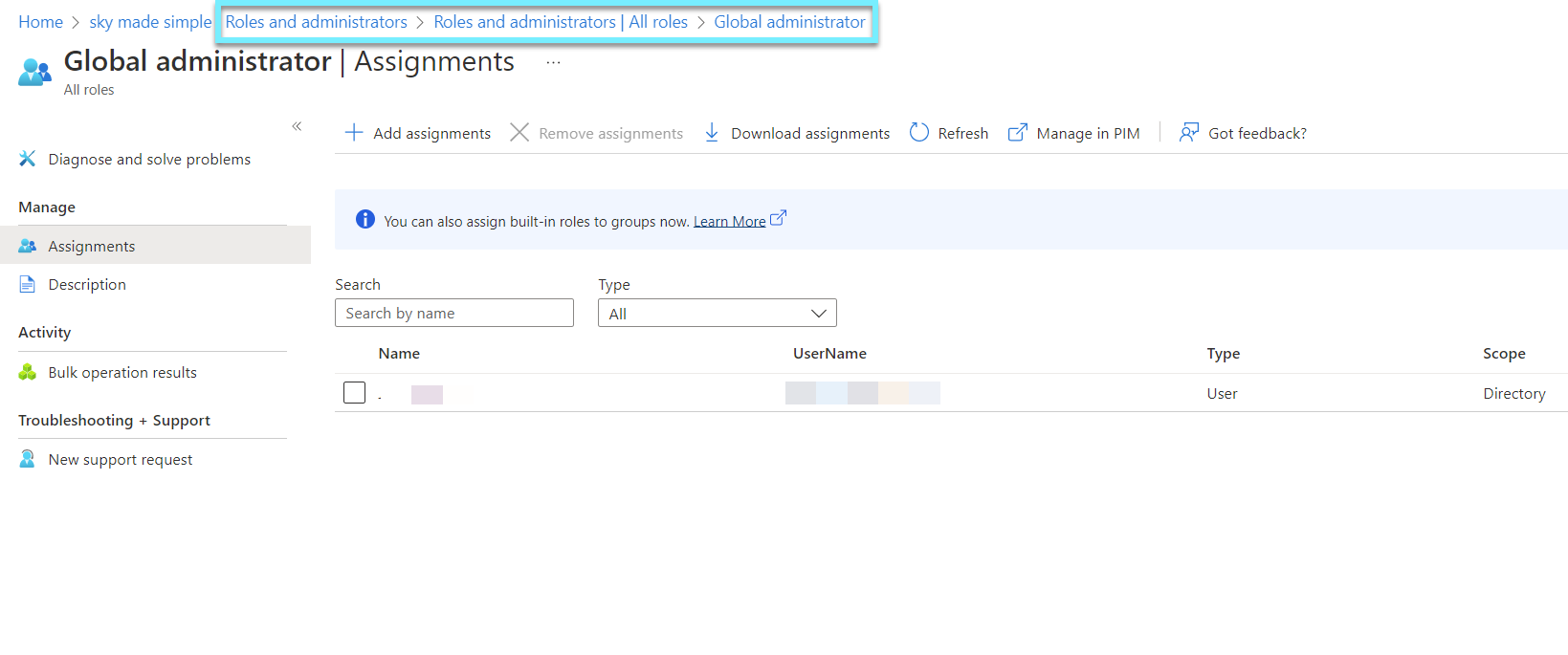
Option 1 - Roles and administrators
By going to Azure AD and Roles and administrators search for Global Admin, we can look for users in our tenant and see who is a Global Administrator (GA).
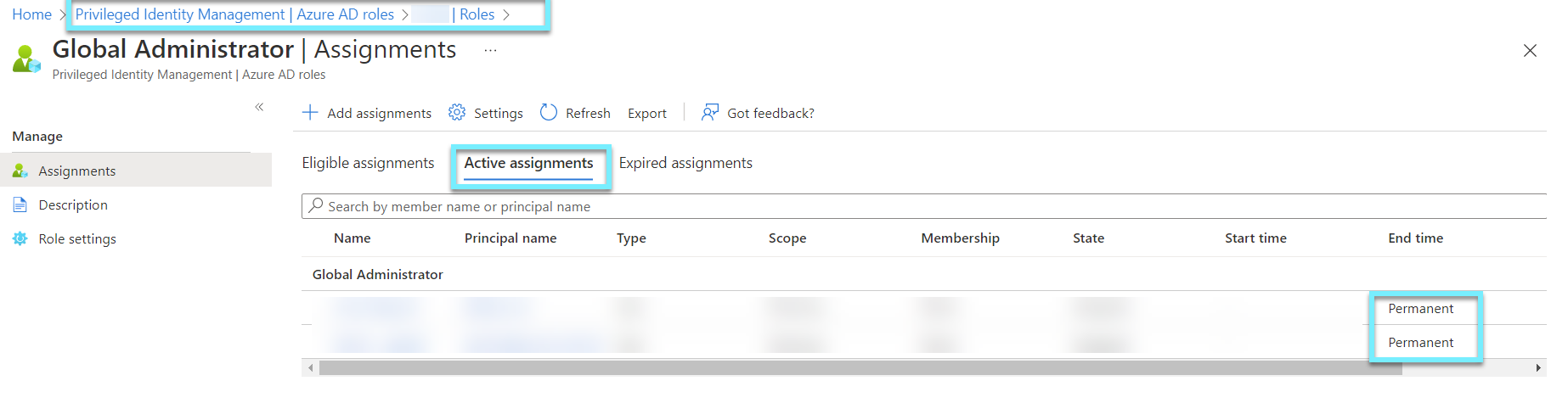
Option 2 - Privileged Identity Management
If we have Azure AD P2, we can use Privileged Identity Management (PIM) to find out who the GA is. If you want users to be able to use GA, you should never make them permanent. Instead, they should only be able to use it if a second approver and a good reason are given.
Enable conditional access policies to block legacy authentication
⚠️The best way to protect your environment is to block legacy/basic authentication and instead use the new authentication standards that come with Primary Refresh Token (PRT). By turning off legacy authentication, we turn on Modern Authentication by default, since we sign in to our SaaS apps with Azure AD. We can quickly stop legacy authentication by using the Conditional Access templates. Just be careful and set it to report only if you need an overview first.
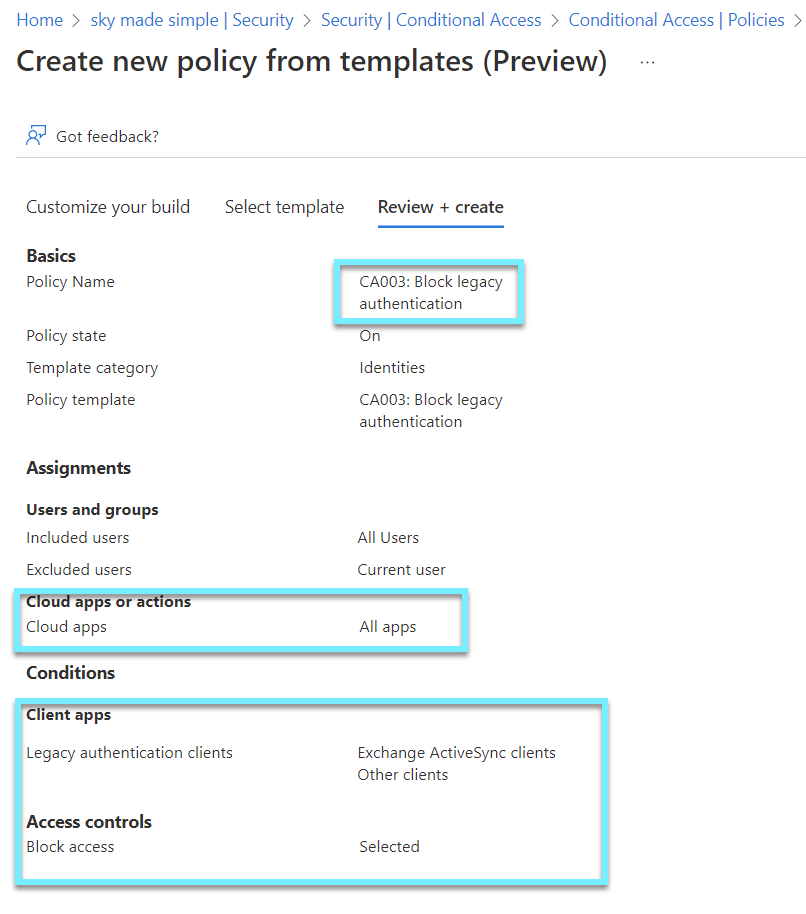
Read my post if you want to find out what a primary refresh token is.

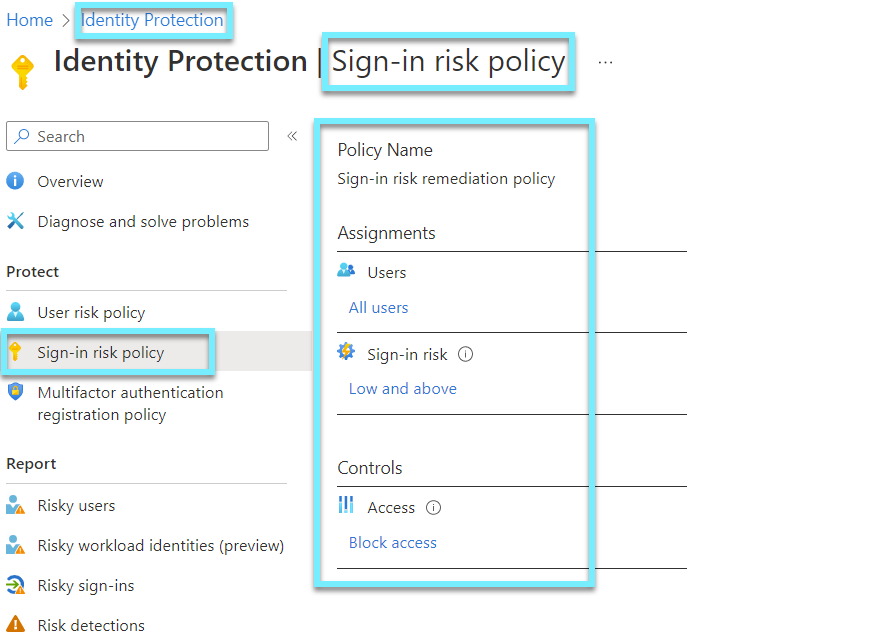
Enabled identity protection to identify anomalous logon behavior
To see anomalous logon behavior we will need Azure P2, which includes Identity Protection to show us User risk and Sign-in risk. What the control is requiring is logon behavior which goes under Sign-in risk. Identity Protection is able to do the following:
- Automate how identity-based risks are found and fixed.
- Use the data in the portal to look into risks.
- You can send data about risk detection to other tools.
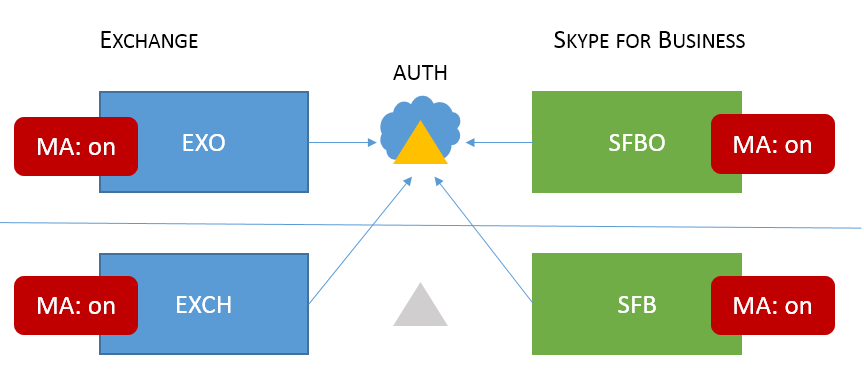
Ensure modern authentication for Exchange Online, Sharepoint and Skype for Business is enabled
Enabling Modern Authentication (MA) for Exchange Online (EXO), Sharepoint(SP), Skype for Business (SFB) will give us the possibility to challenge our users with different kind of conditions and access policies especially for our internet facing application.
Here is the per service state of modern authentication by default for tenants created before August 1, 2017:
- Skype for Business Online - OFF by default.
- Exchange Online - OFF by default.
- SharePoint Online - ON by default.
Related CIS version 8 controls: 6.3 Require MFA🟢 for Externally-Exposed Applications Require all externally-exposed enterprise or third-party applications to enforce MFA, where supported. Enforcing MFA through a directory service or SSO✅ provider is a satisfactory implementation of this Safeguard.
Required
- Single-Sign On = ✅
- Multi-Factor Authentication = 🟢
Not required but recommended
- Conditional Access = 👮
- Moderen approach = 👌
- Legacy = 🪨
Ensure modern authentication for Exchange Online is enabled
EXO is a native Microsoft SaaS, which natively supports Modern Authentication. Whenever you gain access, token-based authentication is used so long as you authenticate via Azure AD. Legacy option would be EXO Hybrid Modern Authentication.
- Exchange Online Hybrid Modern Authentication 🪨✅🟢👮
- Exchange Online as SaaS only 👌✅🟢👮
Ensure modern authentication for Skype for Business is enabled
If you use SFB, you are either using Cloud-only (Skype for Business Online and Azure AD Auth) or on-premises this is where it can get a bit tricky, but the recommendation is using Skype for Business Hybrid Modern Authentication.
- Skype for Business Hybrid Modern Authentication 🪨✅🟢👮
- Skype for Business Online 👌✅🟢👮
Skype for Business
Connect to Skype for Business Online using remote PowerShell, run the following command:
- Allowed Verify that the change was successful by running the following: Get-CsOAuthConfiguration

Skype for Business Hybrid Modern Authentication
Connect to your Exchange on-prem servers and run the following command:
- Get-OrganizationConfig | ft OAuth*
- If the value of the OAuth2ClientProfileEnabled property is False, then modern authentication is disabled.
Recommend following Microsoft documentation if disabled.

Ensure modern authentication for Sharepoint is enabled
Sharepoint (SP) we are able to host our sites on-prem or in the cloud, if we are using Sharepoint in the cloud it is called Sharepoint Online (SPO) and supports natively Modern Authentication with Azure AD, or we are hosting it on-prem.
- SharePoint Server with Microsoft Azure Active Directory (Azure AD)✅🟢👮
- Sharepoint Online 👌✅🟢👮
SharePoint Server with Microsoft Azure Active Directory (Azure AD)
Federated authentication between Azure Active Directory and SharePoint on-premises. The goal is to allow users to sign in on Azure Active Directory and use their identity to access the SharePoint on-premises sites.

Conditional Access Policy for Office 365 (EXO, SP, SfB)
If we are authenticated via Azure AD, you should have a conditional access policy in place that includes either each individual cloud application or Office 365, which includes multiple native Microsoft SaaS.
The Office 365 cloud app makes it possible to target services all at once. Microsoft recommend using the new Office 365 cloud app, instead of targeting individual cloud apps to avoid issues with service dependencies.
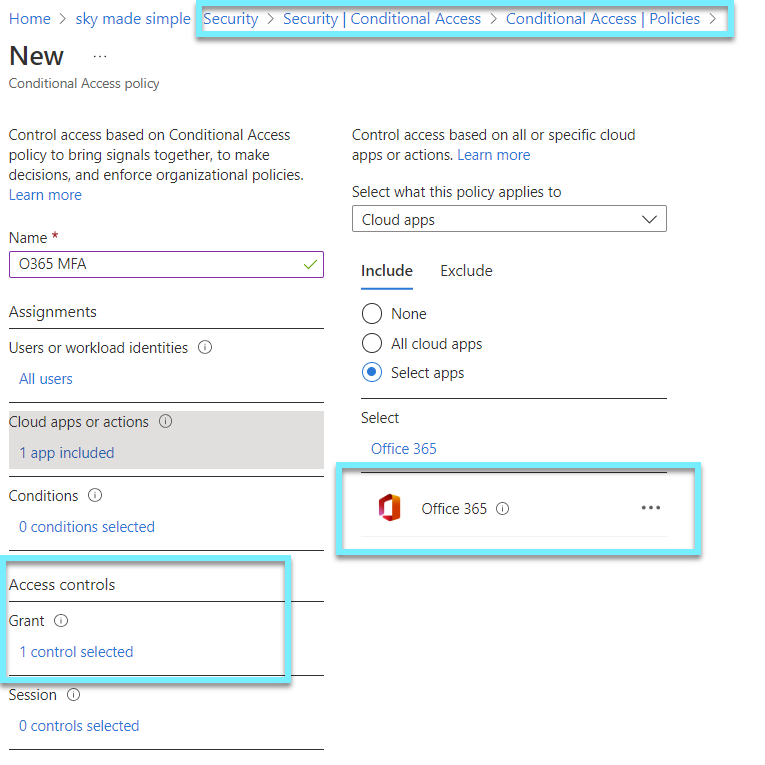
If you are unsure whether users are being prompted for MFA, I suggest reading my previous post.

Ensure multifactor authentication is enabled for all users in administrative roles
To enable MFA for administrative roles, create a Conditional Access from the template library. Run your policies in report-only mode to see the impact.
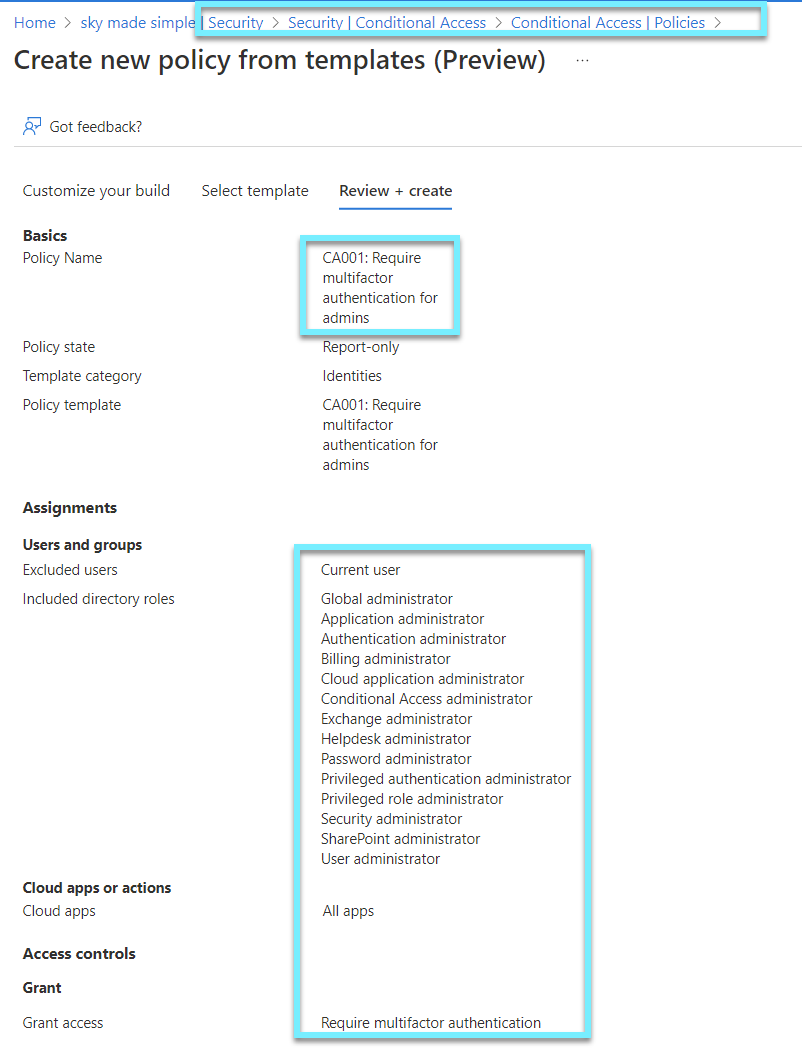
Ensure security defaults is disabled on Azure Active Directory
Tenants created before October 2019 do not have Security Defaults enabled default. If you disable Security Defaults, ensure Conditional Access is in place so that your tenant is not exposed. Here, you can verify if Security Defaults is enabled.
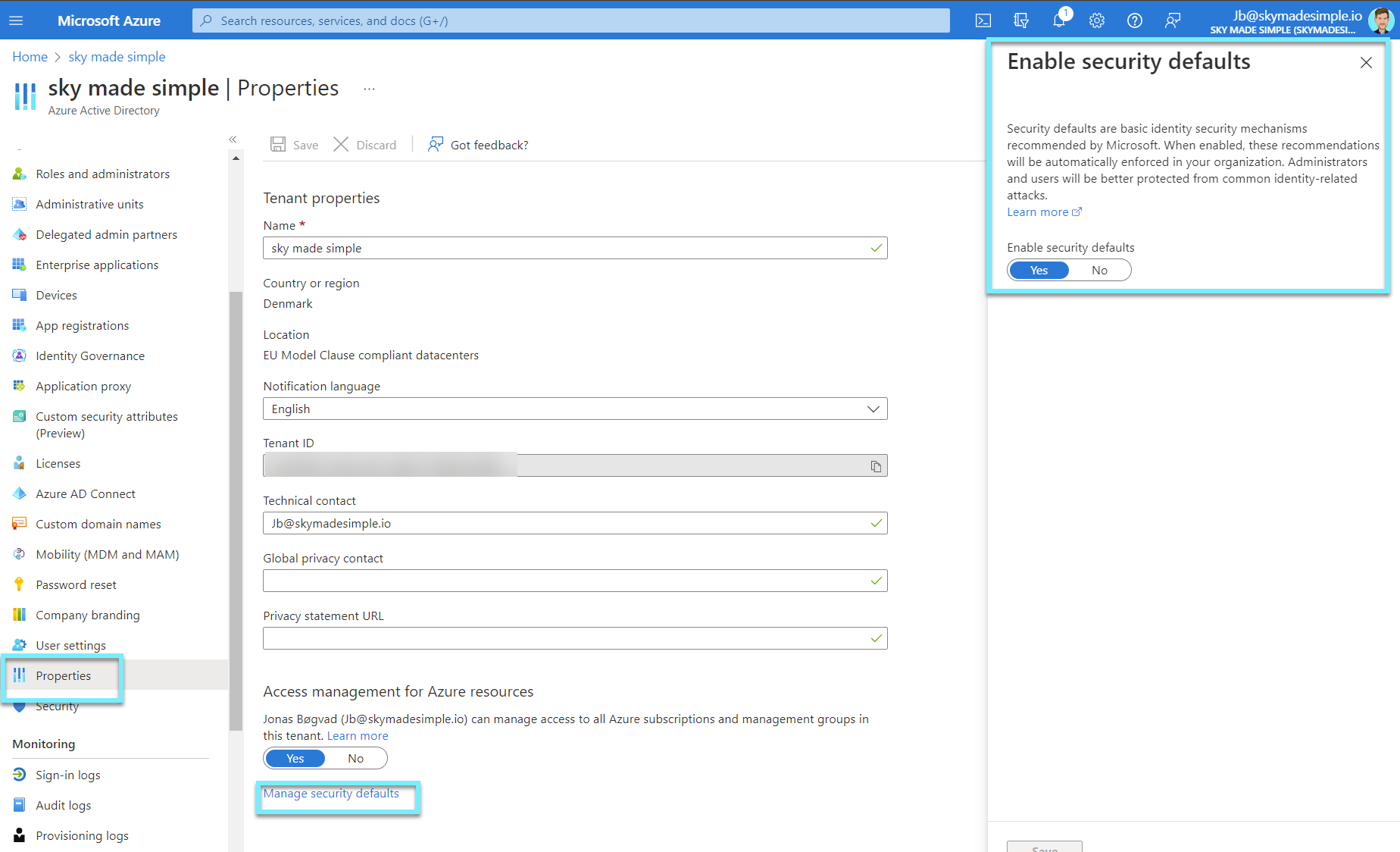
The new security defaults will help protect enterprise user accounts from password spray and phishing attacks by:
- Requiring all users and admins to register for MFA using the Microsoft Authenticator app.
- Challenging users with MFA, mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients that can't do MFA.
- Protecting admins by requiring extra authentication every time they sign in.
Ensure self-service password reset is enabled
Self-service password reset (SSPR) in Azure Active Directory (Azure AD) enables users to change or reset their password without administrator or help desk assistance. If Azure AD locks a user's account or they forget their password, they can unblock themselves and resume work by following on-screen instructions.
Recommend setting it to Selected if disabled ⚠️
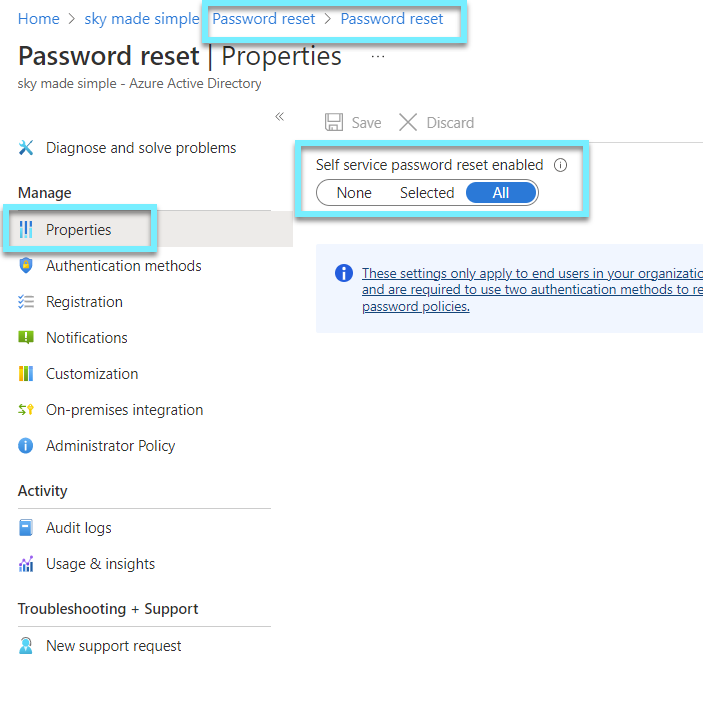
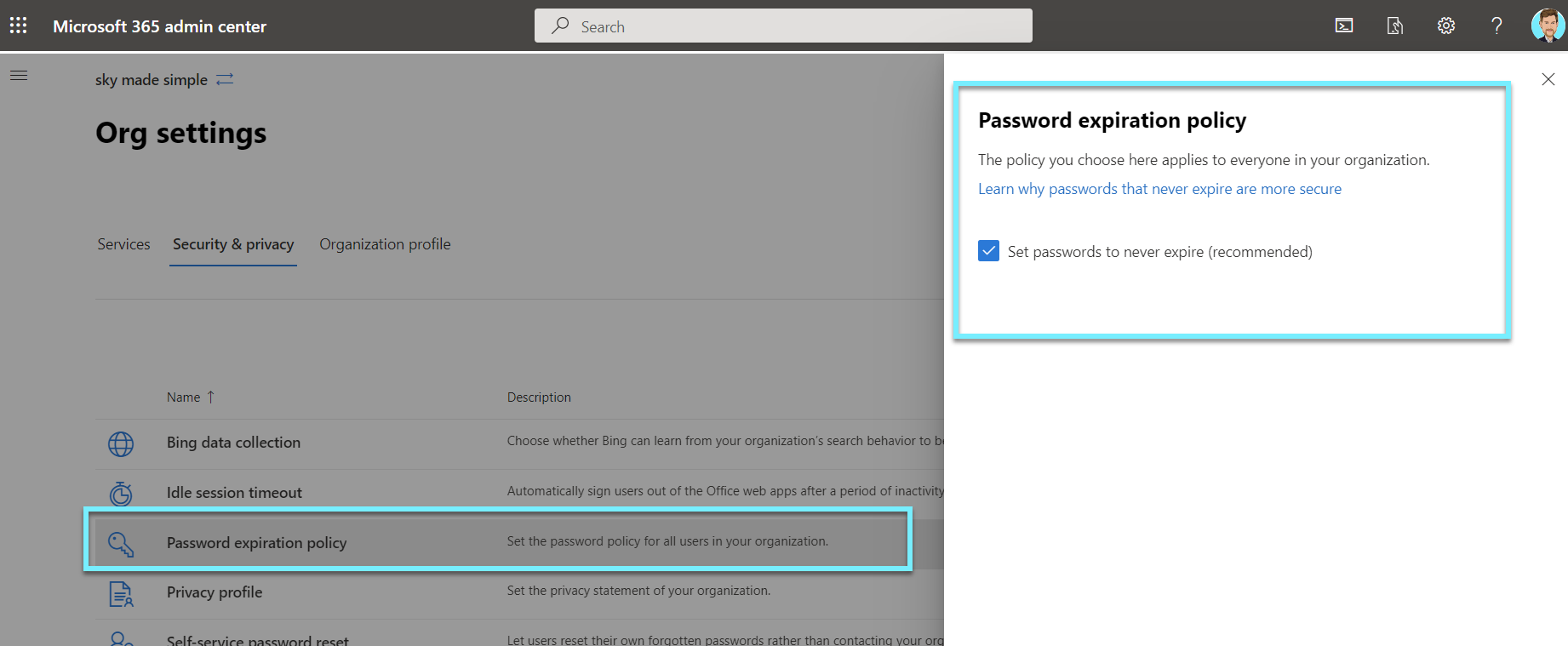
Ensure that Office 365 passwords are not set to expire
Current research indicates that mandated password changes are counterproductive. They encourage users to select weaker passwords, reuse passwords, or update old passwords in a manner that is easily guessed by hackers.
- Go to https://go.microsoft.com/fwlink/p/?linkid=2072756
- Find Password expiration policy
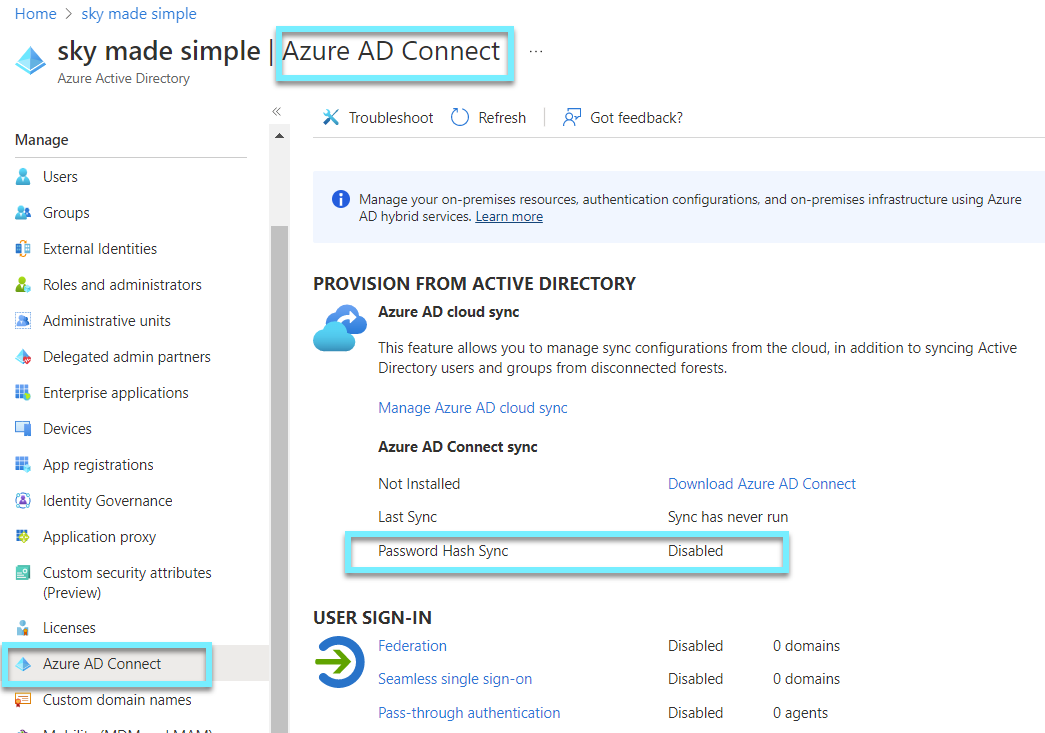
Ensure that password hash sync is enabled for resiliency and leaked credential detection
Synchronization of the password hash is one of the sign-in methods used to achieve hybrid identity. Azure AD Connect synchronizes a user's password hash from an on-premises Active Directory tenant to an Azure AD tenant in the cloud.
You are able to check if Password hash sync is enabled by connecting to your AD Connect or by Azure AD.
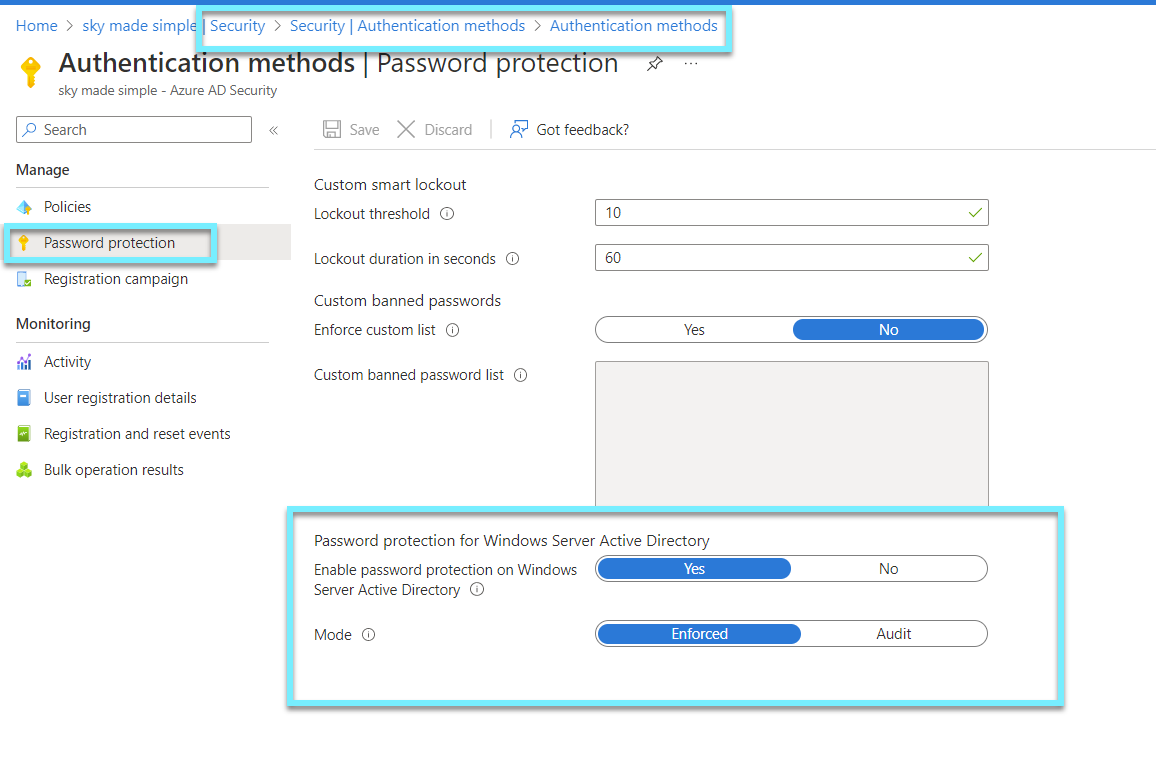
Ensure that password protection is enabled for Active Directory
If you are using hybrid identitets you need to ensure that password protection for Active Directory on-prem is enabled and setup⚠️
More information







