
For starters, what is Passkeys?
Table of Contents
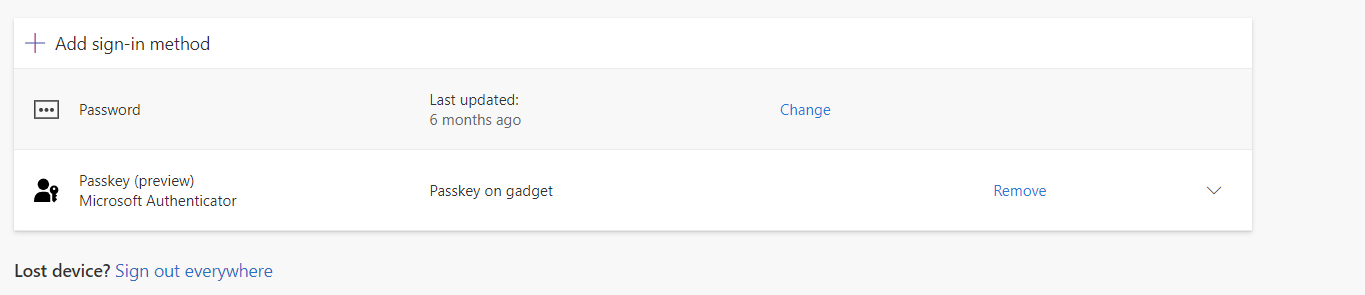
You've most likely heard about passkeys, but have you seen this screenshot before? We hope to see it in Entra ID at some point. Eliminating data fields for storing password strings must be more secure than merely preventing the use of a password with Conditional Access if we are true to Zero Trust.

On September 15, 2021, Microsoft introduced the possibility of removing passwords from our personal accounts. Now, I am looking forward to seeing the same thing happen for our Entra ID accounts, with passkeys leading the way. Let's understand what it is.
Passkeys in Entra ID is in Public Preview
How do Passkeys work?
Passkeys rely on public key cryptography, which pairs a private key stored securely on a device with a public key sent to a web server. When someone signs in to an account their private key is verified against your app or website’s public key. This private key never leaves their device, ensuring that apps and websites never have access to it, and cannot lose it or reveal it in a hacking or phishing attempt. The public key by itself, is not sensitive and does not grant access to anything until it is paired with its corresponding private key stored on a device.
Quick facts: (Credit to https://webauthn.me/passkeys)
- As a FIDO credential, a passkey is a key pair that uses standard public key cryptography to prove a user's identity without sharing any secrets. This is the same approach used in the WebAuthn authentication flow.
- WebAuthn is one of the FIDO 2 specifications that enables passkey support in browsers.
- Device-bound passkeys are also known as single-device passkeys, what we have in Entra. They are bound to the specific device on which they were created. This means that the private key can't leave that device and you can't copy it.
- Synced passkeys, also known as multi-device passkeys, are not tied to a single device. They can be shared across devices and synchronized to a user's cloud account.
Watch how to sign in to portal.office.com using Passkeys.
Passkeys are a replacement for passwords. They are much more secure because they are guaranteed to be strong and unique for each app or website and are extremely resistant to phishing attacks. The concept of Bob and Alice in is now popular again.
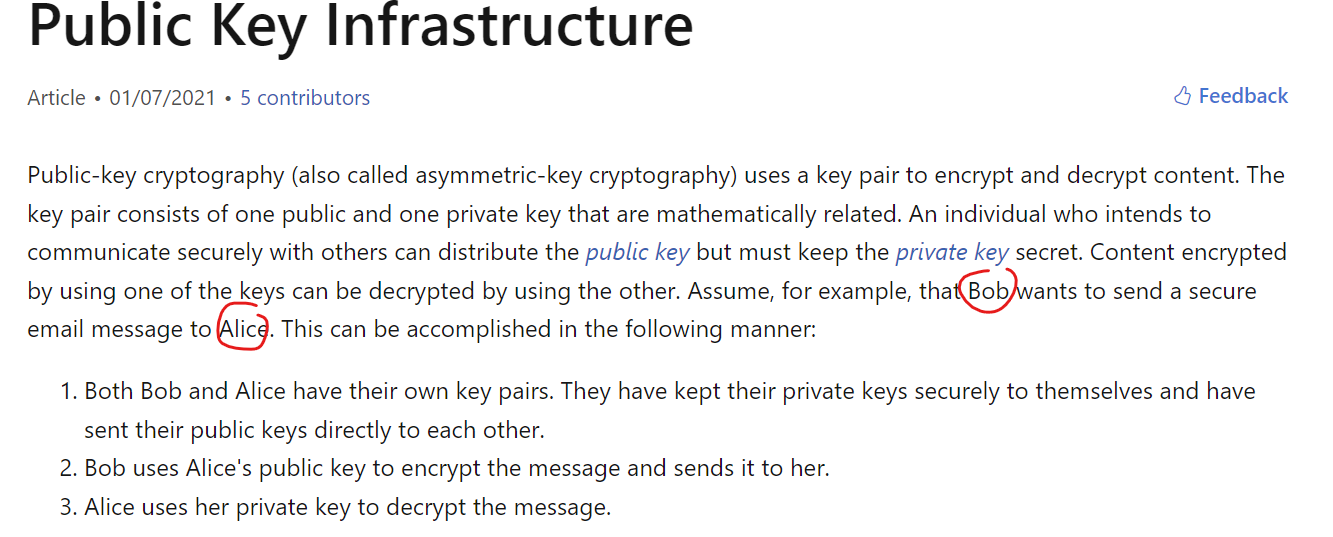
💡 Public-key cryptography uses a key pair to encrypt and decrypt content. This key pair consists of one public and one private key that are mathematically related.
What do the Internet say?

I bet you know who Shopify is, and they say:
Eliminate the need for passwords and two-factor authentication by letting customers verify their identity with biometrics, a PIN, or by drawing a pattern with their finger.
Google tells us it's as easy as 1-2-3.
Even PayPal is providing us with a better alternative to protect our 💸
Passkeys are a new secure login standard created by the FIDO Alliance and the World Wide Web Consortium. A passkey allows you securely log in to PayPal without entering a password.
Not to forget Apple! They say it's "Next-generation account security."
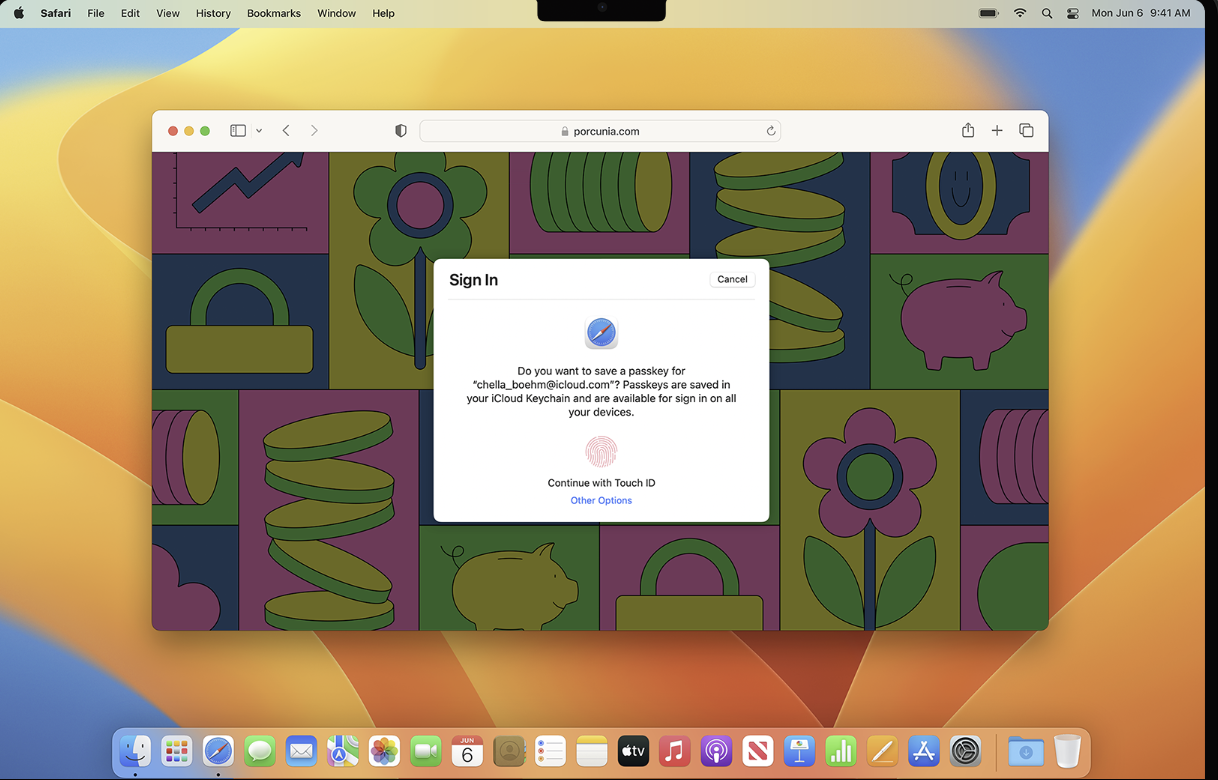
Now that we understand how passkey authentication works and the possibilities we have with Entra ID, we are now able to authenticate with passkeys. Microsoft just released it in public preview, so we are now able to test it ourselves.
FIDO Alliance has some etablished companies as board members and many more!

Create a Passkey
Screenshots here:

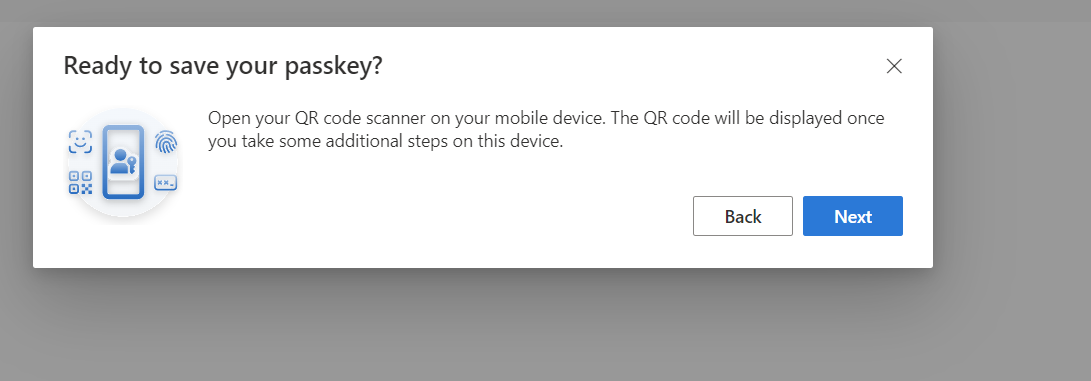


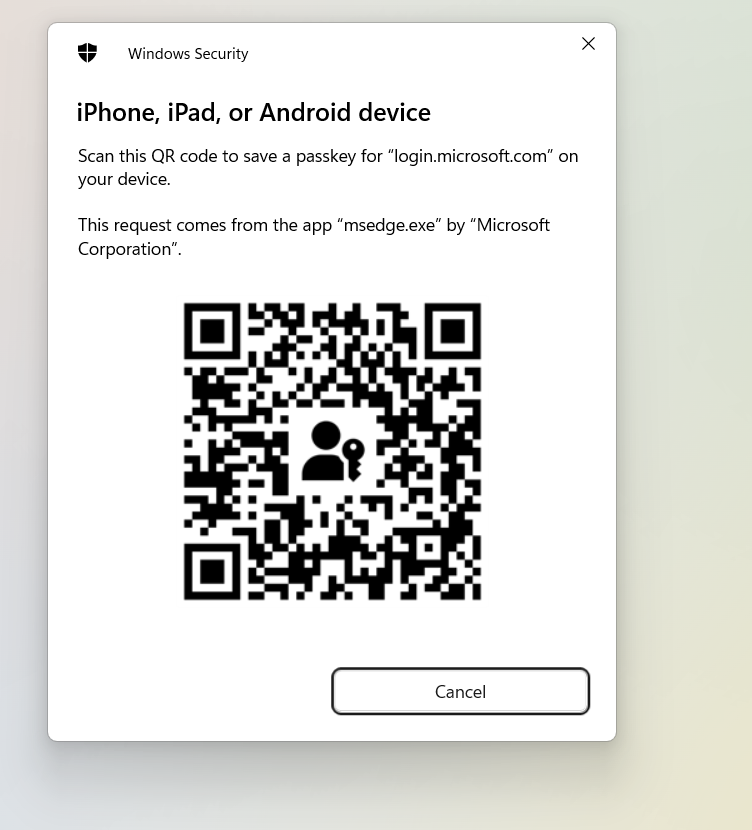
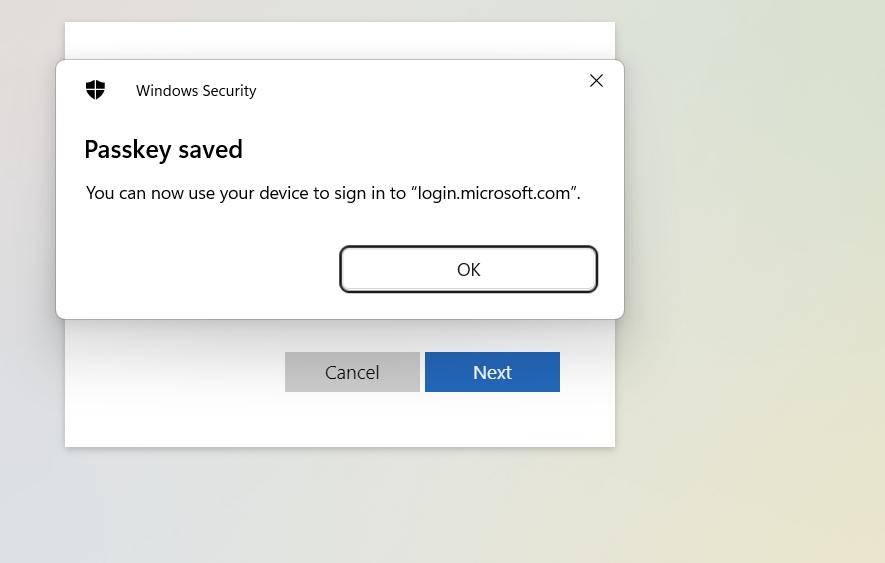
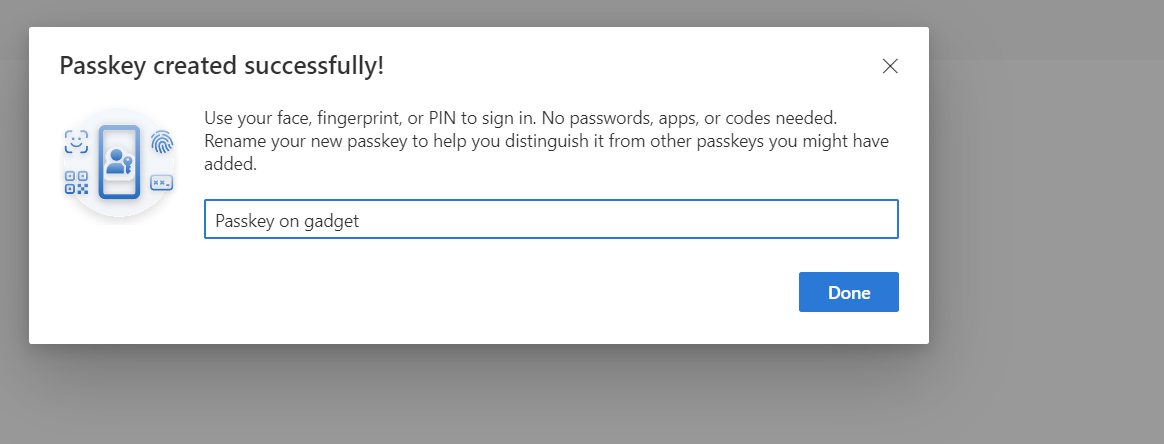
Enable the Public Preview
For test, you can opt-in to this public preview, but you will need access to Entra ID with at least "Authentication Policy Administrator". Don't forget to be thoughtful and do your testing first in a sandbox environment.
⚠️ Note: I do not recommend setting "Enforce attestation" to "No" in a production environment. Read more below.
Go to Entra.microsoft.com and follow the screenshot.
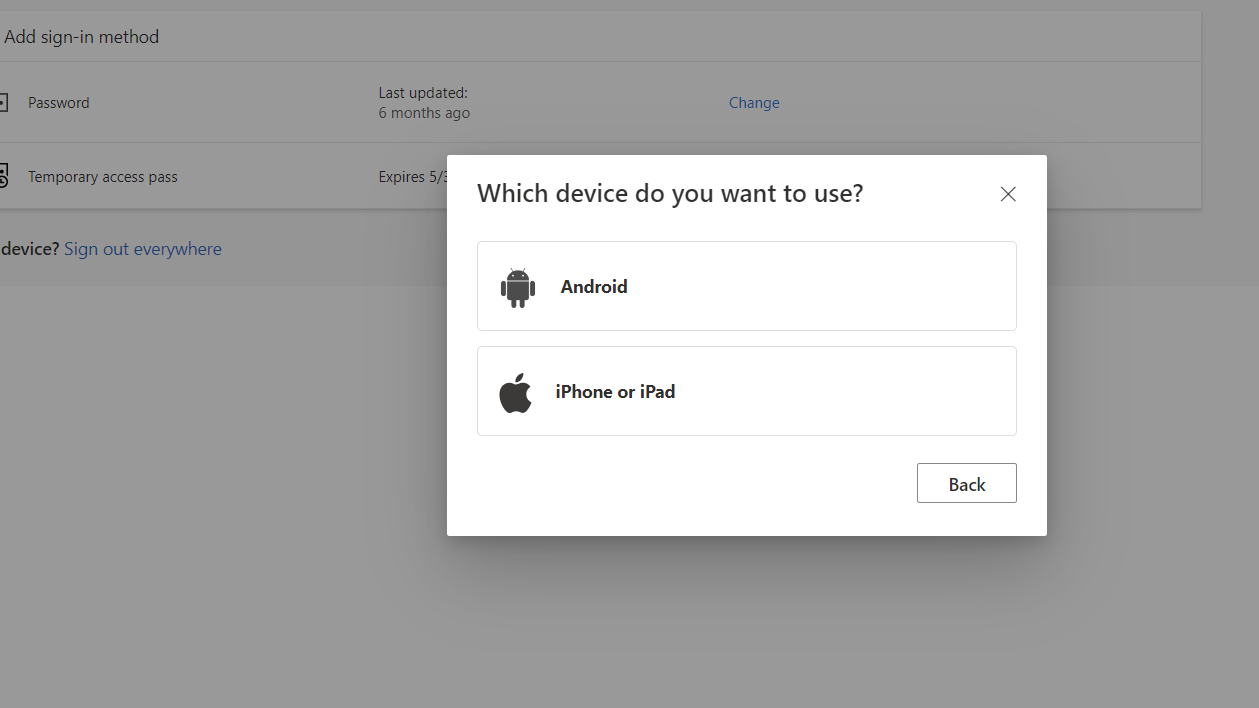
- Authenticator for iOS: 90a3ccdf-635c-4729-a248-9b709135078f
- Authenticator for Android: de1e552d-db1d-4423-a619-566b625cdc84

This will give you the option to choose:
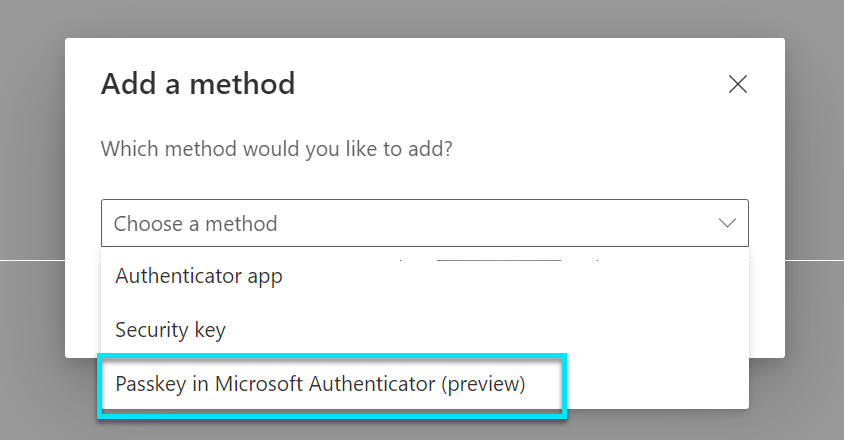
So now you are able to setup passkey in the MS Auth app, but lets quickly dig into what it means to set "Enforce attestation to No(5)" and "restrict Specific keys(6)".
- Enforce Attestation should be set to "Yes" if your organization wants assurance that a FIDO2 security key model or passkey provider is genuine and comes from a legitimate vendor.
- Enforce Key Restrictions should be set to "Yes" only if your organization wants to allow or disallow certain security key models or passkey providers, which are identified by their Authenticator Attestation GUID (AAGUID). You can work with your security key vendor to determine the AAGUID of the passkey. If the passkey is already registered, you can find the AAGUID by viewing the authentication method details of the passkey for the user.
Enforce attestation and Restrict specific keys bad idea
Combining "Enforce attestation" set to "No" with "Restrict Specific Keys" can be problematic. Without attestation enforcement, there's no verification that the device generating or storing the keys is authentic, even if specific keys are restricted. Which means there's no guaranteed verification that the device is genuine as represented by the AAGUID.


